Be the first to see our latest product releases—virtually—at Redis Released: Worldwide.
Register now
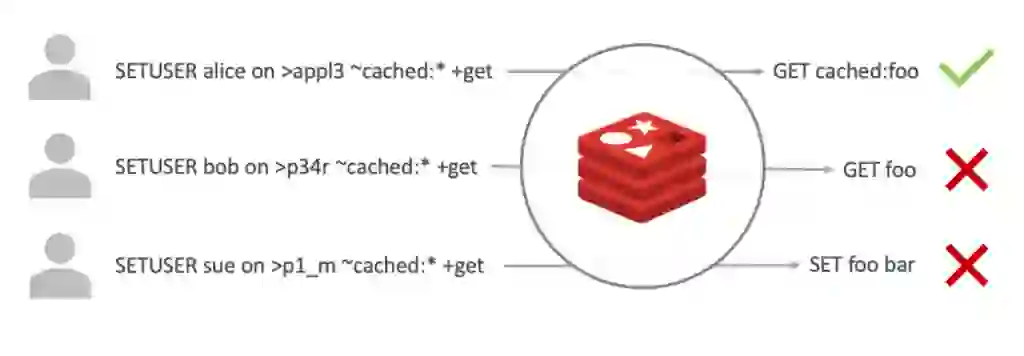
Enforce least-privilege access using access control lists (ACLs) for keys and commands.
Redis Enterprise can help protect your data through its entire lifecycle.
Ensure compliance and accountability with Redis Enterprise’s full audit log of administrative actions.
Redis Enterprise comes with enhanced disaster-recovery features, including resource limits and advanced clustering and sharding.
Implement geographically distributed disaster recovery and high availability (99.999%) strategies with Redis Cloud.
Redis Enterprise can integrate with your external identity provider for its control plane access so you can enforce your security policies.
Redis Enterprise removes the configuration complexity of securing Redis. Using role-based access control (RBAC), you never have to provision a persona twice. Simplify Redis security using built-in and customizable access controls assigned based on a user’s role—even across multiple databases.
Redis Enterprise hardens Redis by blocking commands and is designed to help protect against out-of-memory events and Lua scripts from accessing the host operating system. The result? Spend less time worrying about preventing attacks and more time developing innovative applications.
Redis Enterprise helps you sleep at night. With sharding and failover strategies, built-in capabilities to migrate shards between nodes, and protection from out-of-memory events, Redis Enterprise has got your back.
Reduce the cost of mistakes by implementing the principle of least privilege. Robust role-based access control helps ensure that developers and admins don’t accidentally—or on purpose—drop your database.
Watch our recent Tech Talk — Buy vs Build: Security & access management in Redis Open Source vs. Redis Enterprise