Enable TLS
Shows how to enable TLS.
You can use TLS authentication for one or more of the following types of communication:
- Communication from clients (applications) to your database
- Communication from your database to other clusters for replication using Replica Of
- Communication to and from your database to other clusters for synchronization using Active-Active
Enable TLS for client connections
To enable TLS for client connections:
-
From your database's Security tab, select Edit.
-
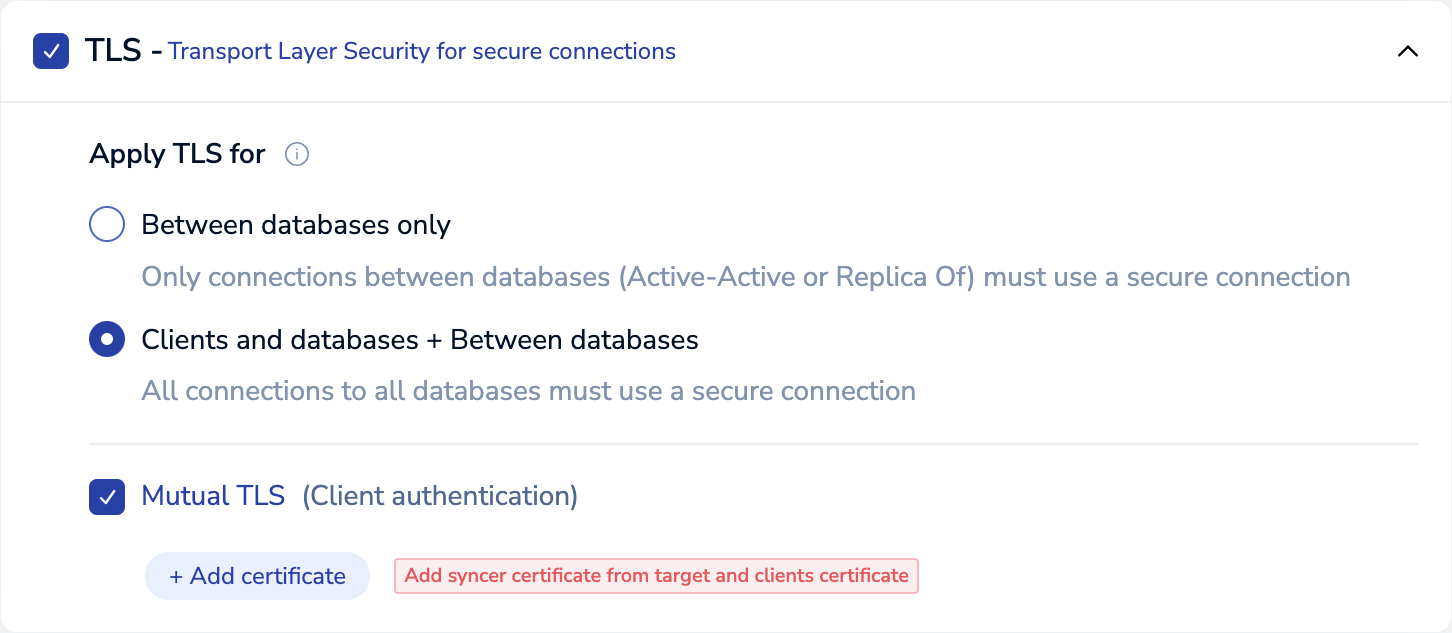
In the TLS - Transport Layer Security for secure connections section, make sure the checkbox is selected.
-
In the Apply TLS for section, select Clients and databases + Between databases.
-
Select Save.
To enable mutual TLS for client connections:
-
Select Mutual TLS (Client authentication).
-
For each client certificate, select + Add certificate, paste or upload the client certificate, then select Done.
If your database uses Replica Of or Active-Active replication, you also need to add the syncer certificates for the participating clusters. See Enable TLS for Replica Of cluster connections or Enable TLS for Active-Active cluster connections for instructions.
-
You can configure Additional certificate validations to further limit connections to clients with valid certificates.
Additional certificate validations occur only when loading a certificate chain that includes the root certificate and intermediate CA certificate but does not include a leaf (end-entity) certificate. If you include a leaf certificate, mutual client authentication skips any additional certificate validations.
-
Select a certificate validation option.
Validation option Description No validation Authenticates clients with valid certificates. No additional validations are enforced. By Subject Alternative Name A client certificate is valid only if its Common Name (CN) matches an entry in the list of valid subjects. Ignores other Subjectattributes.By full Subject Name A client certificate is valid only if its Subjectattributes match an entry in the list of valid subjects. -
If you selected No validation, you can skip this step. Otherwise, select + Add validation to create a new entry and then enter valid
Subjectattributes for your client certificates. AllSubjectattributes are case-sensitive.Subject attribute
(case-sensitive)Description Common Name (CN) Name of the client authenticated by the certificate (required) Organization (O) The client's organization or company name Organizational Unit (OU) Name of the unit or department within the organization Locality (L) The organization's city State / Province (ST) The organization's state or province Country (C) 2-letter code that represents the organization's country You can only enter a single value for each field, except for the Organizational Unit (OU) field. If your client certificate has a
Subjectwith multiple Organizational Unit (OU) values, press theEnterorReturnkey after entering each value to add multiple Organizational Units.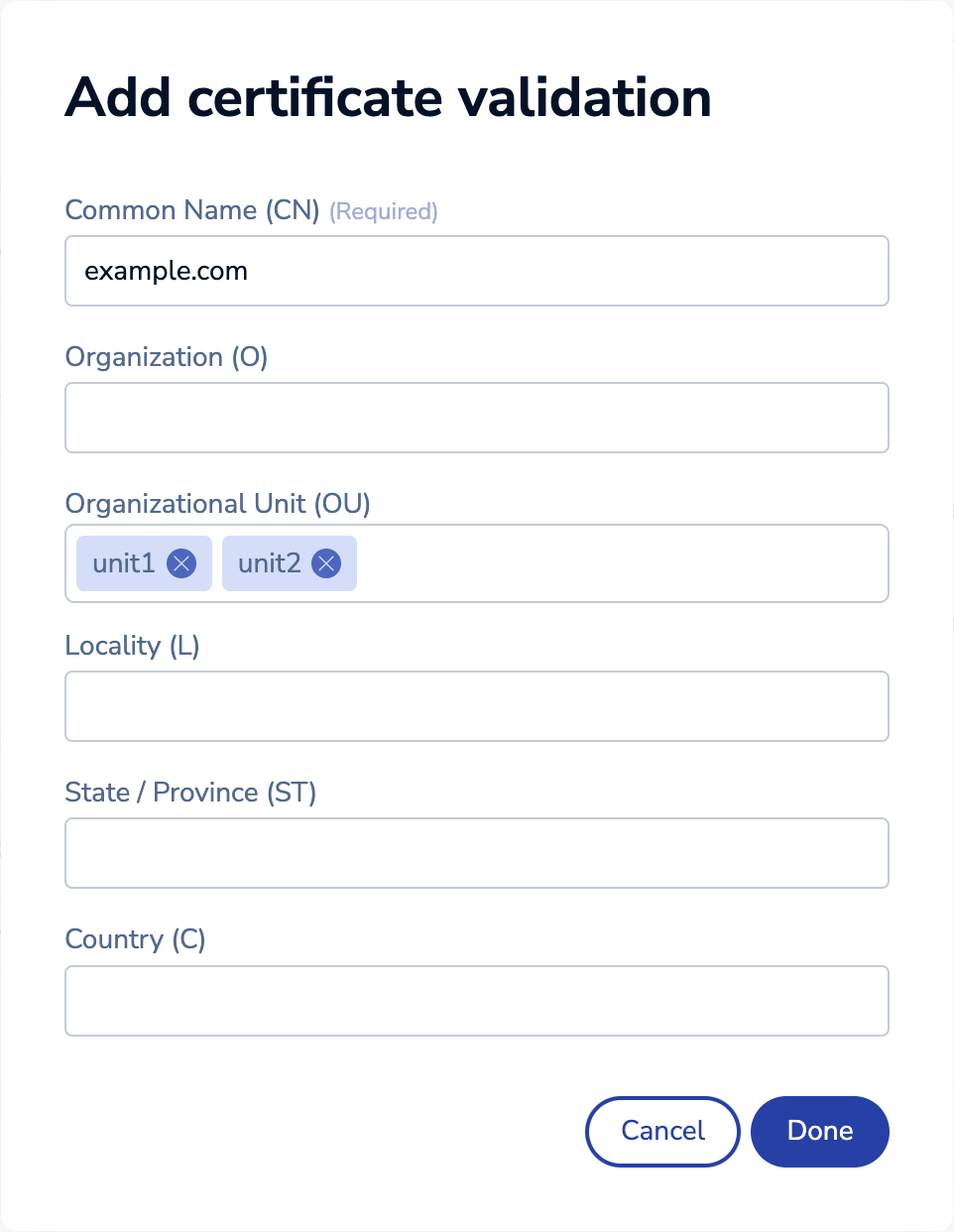
Breaking change: If you use the REST API instead of the Cluster Manager UI to configure additional certificate validations, note that
authorized_namesis deprecated as of Redis Enterprise v6.4.2. Useauthorized_subjectsinstead. See the BDB object reference for more details.
-
-
Select Save.
Note:By default, Redis Enterprise Software validates client certificate expiration dates. You can use
rladminto turn off this behavior.rladmin tune db < db:id | name > mtls_allow_outdated_certs enabled
Enable TLS for Active-Active cluster connections
To enable TLS for Active-Active cluster connections:
Retrieve syncer certificates
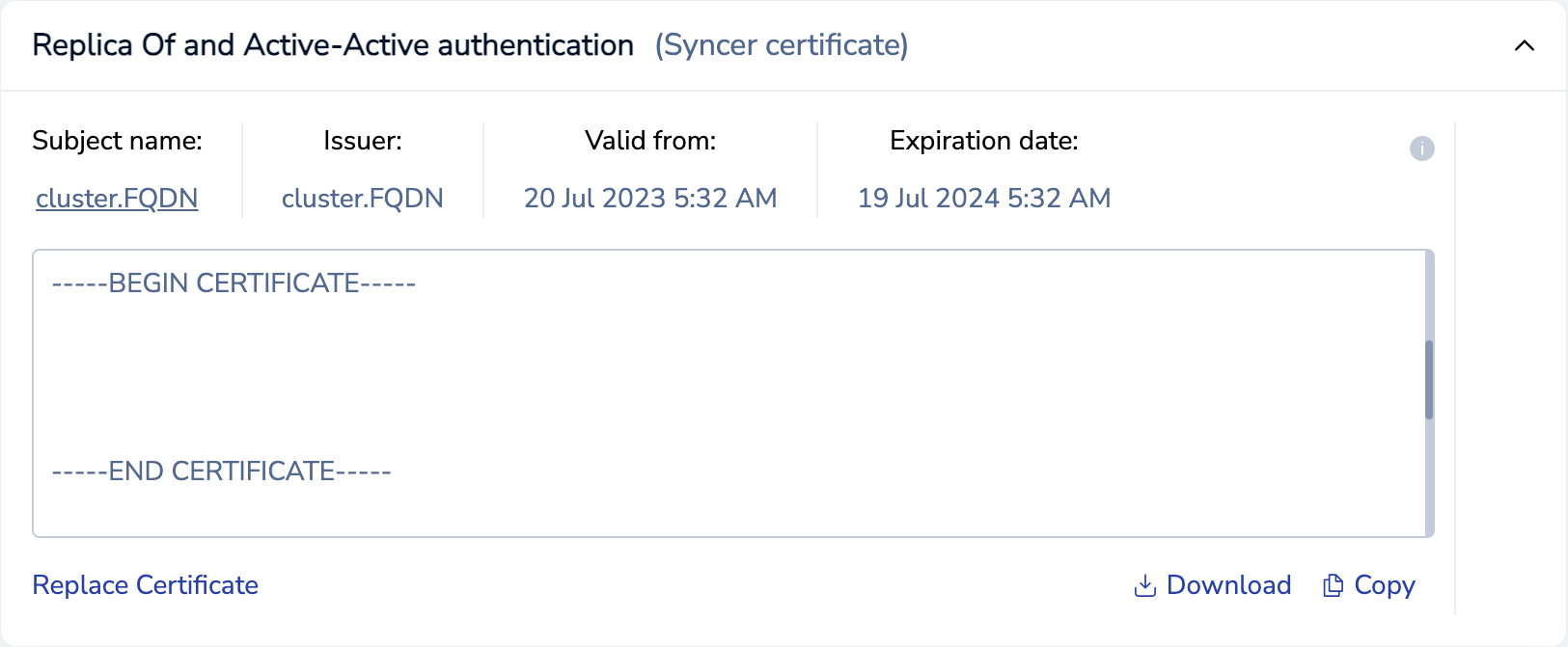
For each participating cluster, copy the syncer certificate from the general settings tab.
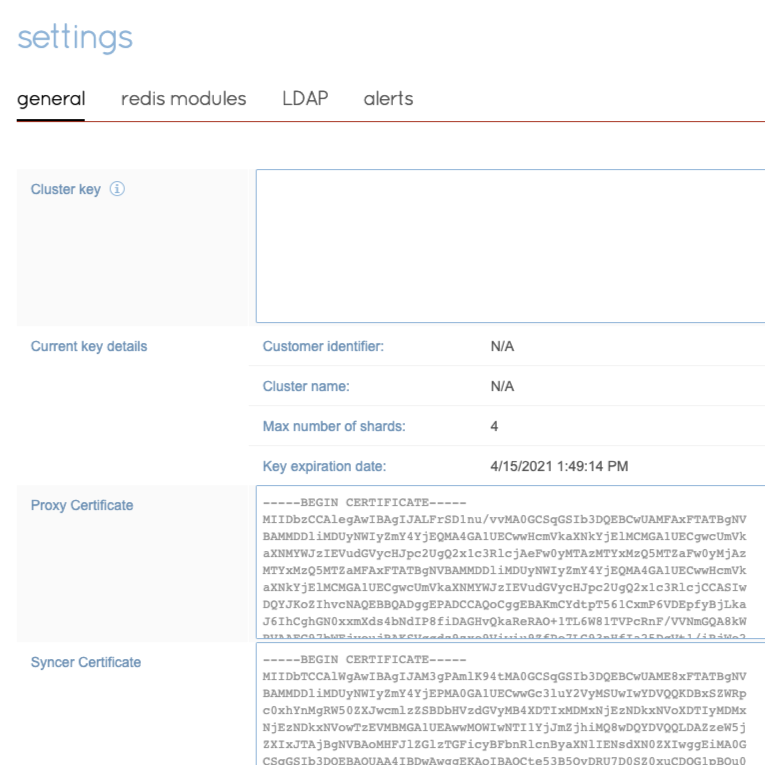
Configure TLS certificates for Active-Active
- During database creation (see Create an Active-Active Geo-Replicated Database, select Edit from the configuration tab.
- Enable TLS.
- Enforce client authentication is selected by default. If you clear this option, you will still enforce encryption, but TLS client authentication will be deactivated.
- Select Require TLS for CRDB communication only from the dropdown menu.
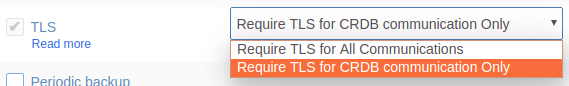
- Select Add

- Paste a syncer certificate into the text box.
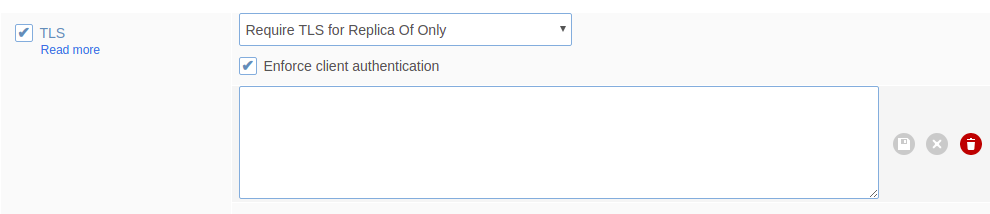
- Save the syncer certificate.

- Repeat this process, adding the syncer certificate for each participating cluster.
- Optional: If also you want to require TLS for client connections, select Require TLS for All Communications from the dropdown and add client certificates as well.
- Select Update at the bottom of the screen to save your configuration.
Configure TLS on all participating clusters
Repeat this process on all participating clusters.
To enforce TLS authentication, Active-Active databases require syncer certificates for each cluster connection. If every participating cluster doesn't have a syncer certificate for every other participating cluster, synchronization will fail.
Enable TLS for Replica Of cluster connections
To enable TLS for Replica Of cluster connections:
-
For each cluster hosting a replica:
-
From the Security tab of the Replica Of source database, select Edit.
-
In the TLS - Transport Layer Security for secure connections section, make sure the checkbox is selected.
-
In the Apply TLS for section, select Between databases only.
-
Select Mutual TLS (Client authentication).
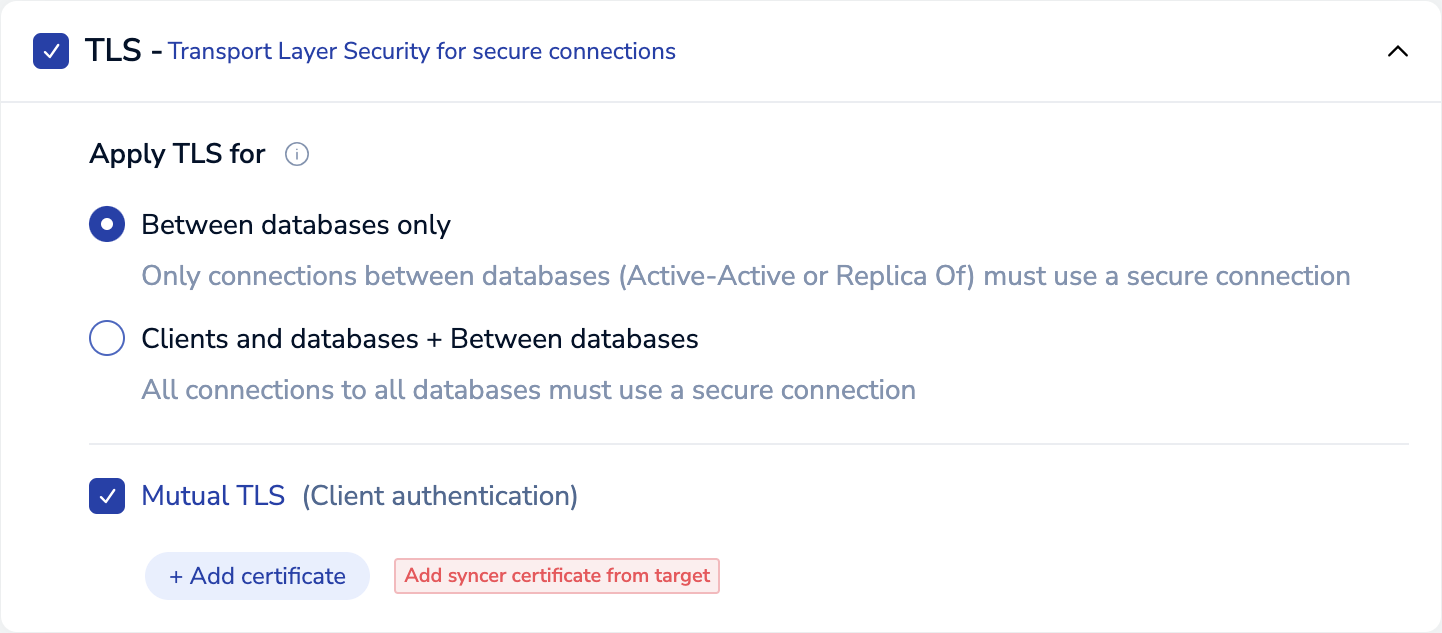
-
Select + Add certificate, paste or upload the syncer certificate, then select Done.
Repeat this process, adding the syncer certificate for each cluster hosting a replica of this database.
-
(Optional) To require TLS for client connections, change Apply TLS for to Clients and databases + Between databases and add client certificates.
-
Select Save.