Authentication Token Storage
Use Redis Enterprise to provide a responsive, scalable, and resilient login process
The login and authentication process is critically important to an application’s user experience and availability. During the login process, after the user has successfully enters their credentials, an authentication server creates an authentication token for the duration of the user session. Redis Enterprise excels as an authentication token store. Its speed enables significantly better login experiences while ensuring mission-critical applications are always available and scale seamlessly. Why not make a good first impression?
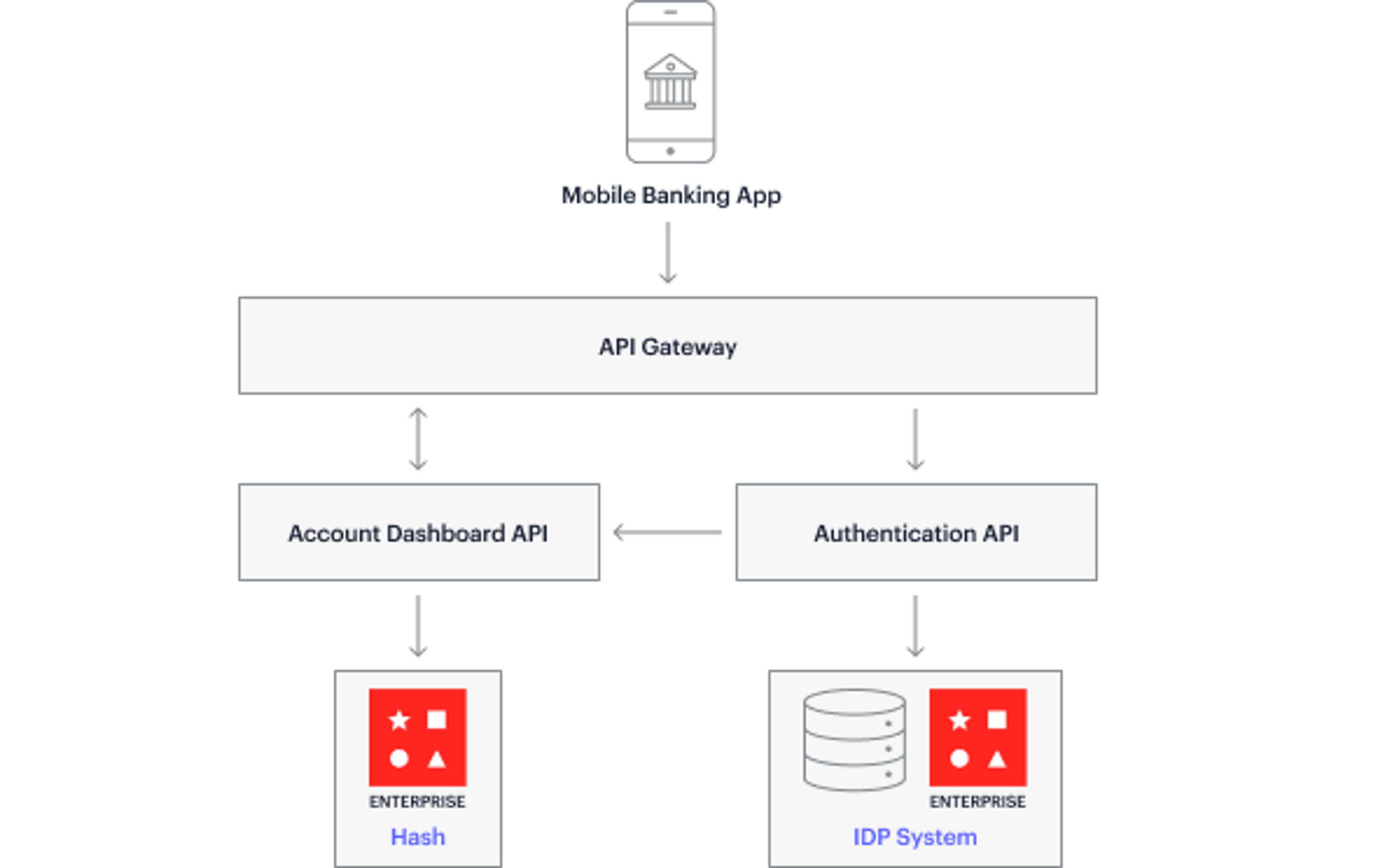
How it works for a mobile banking app
- A user enters their credentials.
- An IDP system (authentication server) validates the user credentials and generates an authentication token.
- That authentication token is stored in Redis Enterprise for the duration of a user session. The app and all its components can consult the token to recognize the user as validated.
Solve your challenges
| The problem | The solution | |
|---|---|---|
| Slow application login and authentication frustrates users and creates a poor first impression. | • | |
| Using Redis for authentication token storage enables applications to provide better login experiences. | • | |
| Difficulty maintaining login and authentication process during periods of peak demand. | • | |
| Redis Enterprise is extremely scalable, enabling flawless login and authentication experiences even during periods of peak demand. | • | |
| Excessive reads cause performance penalties and higher infrastructure costs. | • | |
| Redis Enterprise is highly resilient, with 99.999% uptime. You can be confident that that the login process won’t fail, so your apps are always available to users. | • |
Benefits of authentication token storage
- Sub-millisecond response times to streamline user logins and fast authentication
- A highly scalable authentication system that ensures seamless user logins, even during times of peak demand
- High availability and resilience prevent authentication system problems that cause application outages
Related resources
FAQs
An authentication token is a digital artifact that represents a user’s identity created by an authentication server after an user has successfully entered their credentials. However, insecure authentication token storage can lead to significant application security vulnerabilities.
The token generated by an authentication server can be stored in a relational or noSQL database, a file-based store, or an in-memory. Disk-based relational or NoSQL databases are slow and pose scalability challenges. In-memory stores such as open-source Redis allow fast access and easy management of tokens but do not scale to meet the needs of today’s companies.
So that applications and their components can quickly and securely identify a user as validated during a user session.
Authentication tokens should be stored for the duration of a user session