Create roles with combined access
Create roles with both cluster and database access.
| Redis Software |
|---|
To create a role that grants database access privileges and allows access to the Cluster Management UI and REST API:
-
Define Redis ACLs that determine database access privileges.
-
Create a role with ACLs added and choose a Management role other than None.
Define Redis ACLs
You can use the Cluster Manager UI or the REST API to define Redis ACL rules that you can assign to roles.
To define a Redis ACL rule using the Cluster Manager UI:
-
From Access Control > Roles > Data ACLs, you can either:
-
Select an existing Redis ACL from the list to edit it.
-
Click + Add Redis ACL to create a new Redis ACL.
-
-
Enter a descriptive name for the Redis ACL. This will be used to associate the ACL rule with the role.
-
Define the ACL rule. For more information about Redis ACL rules and syntax, see the Redis ACL overview.
-
Click Save.
failure, but the command runs on the keys that are allowed.Create roles with ACLs and cluster access
You can create a role that grants database access privileges and allows access to the Cluster Management UI and REST API.
To define a role for combined access using the Cluster Manager UI:
-
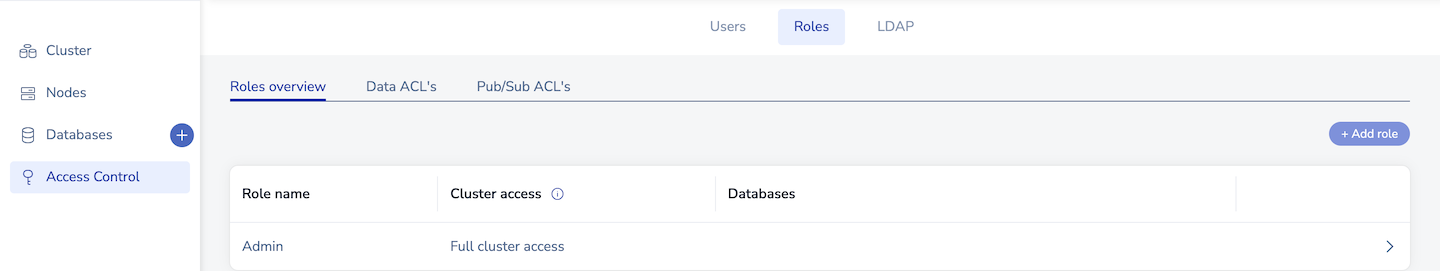
From Access Control > Roles, you can:
-
Select a role from the list of existing roles to edit it.
-
Click + Add role to create a new role.
-
-
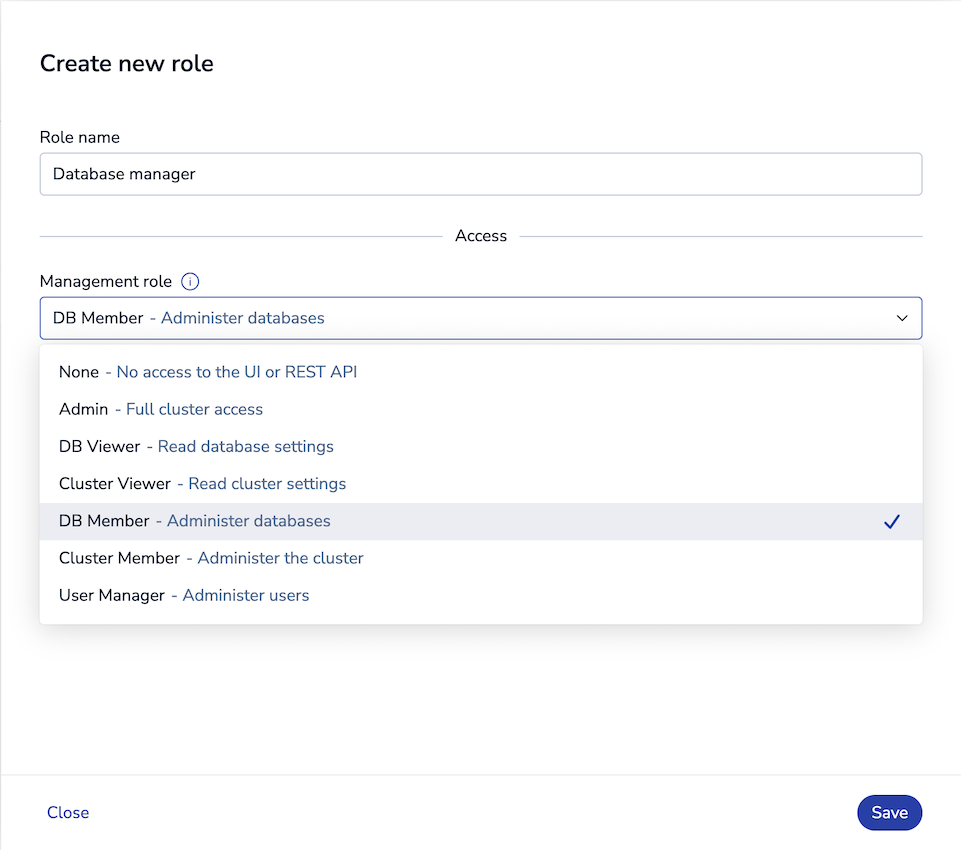
Enter a descriptive name for the role. This will be used to reference the role when configuring users.
-
Choose a Management role other than None. For details about permissions granted by each role, see Cluster Manager UI permissions and REST API permissions.
-
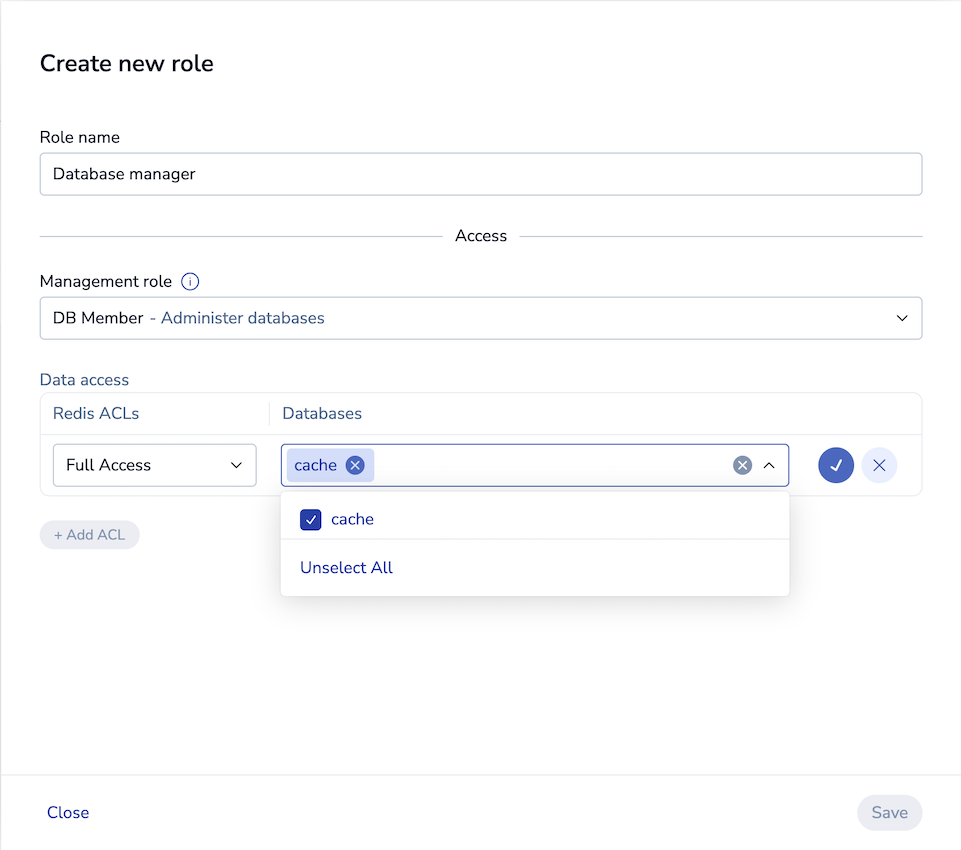
Click + Add ACL.
-
Choose a Redis ACL and databases to associate with the role.
-
Click the check mark to confirm.
-
Click Save.
You can assign the new role to users to grant database access and access to the Cluster Manager UI and REST API.