Configure TLS protocol
| Redis Software |
|---|
You can change TLS protocols to improve the security of your Redis Software cluster and databases. The default settings are in line with industry best practices, but you can customize them to match the security policy of your organization.
Configure TLS protocol
The communications for which you can modify TLS protocols are:
- Control plane - The TLS configuration for cluster administration.
- Data plane - The TLS configuration for the communication between applications and databases.
- Discovery service (Sentinel) - The TLS configuration for the discovery service.
You can configure TLS protocols with the Cluster Manager UI, rladmin, or the REST API.
-
After you set the minimum TLS version, Redis Software does not accept communications with TLS versions older than the specified version.
-
If you set TLS 1.3 as the minimum TLS version, clients must support TLS 1.3 to connect to Redis Software.
TLS support depends on the operating system. You cannot enable support for protocols or versions that aren't supported by the operating system running Redis Software. In addition, updates to the operating system or to Redis Software can impact protocol and version support.
If you have trouble enabling specific versions of TLS, verify that they're supported by your operating system and that they're configured correctly.
Edit TLS settings in the UI
To configure minimum TLS versions using the Cluster Manager UI:
-
Go to Cluster > Security, then select the TLS tab.
-
Click Edit.
-
Select the minimum TLS version for cluster connections, database connections, and the discovery service:
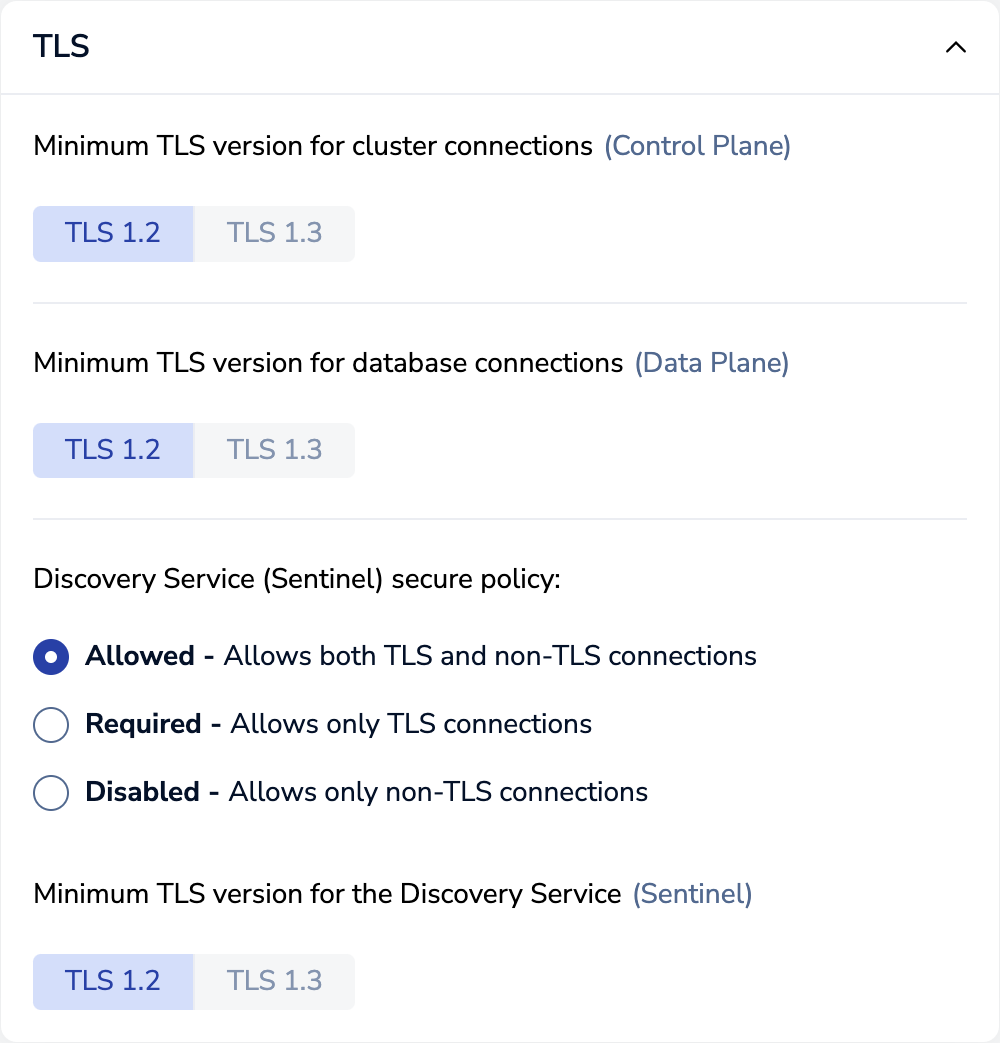
-
Select the TLS mode for the discovery service:
- Allowed - Allows both TLS and non-TLS connections
- Required - Allows only TLS connections
- Disabled - Allows only non-TLS connections
-
Click Save.
Control plane TLS
To set the minimum TLS protocol for the control plane using rladmin:
- Default minimum TLS protocol: TLSv1.2
- Syntax:
rladmin cluster config min_control_TLS_version <TLS_Version> - TLS versions available:
- For TLSv1.2 - 1.2
- For TLSv1.3 - 1.3
For example:
rladmin cluster config min_control_TLS_version 1.2
Data plane TLS
To set the minimum TLS protocol for the data path using rladmin:
- Default minimum TLS protocol: TLSv1.2
- Syntax:
rladmin cluster config min_data_TLS_version <TLS_Version> - TLS versions available:
- For TLSv1.2 - 1.2
- For TLSv1.3 - 1.3
For example:
rladmin cluster config min_data_TLS_version 1.2
Discovery service TLS
To enable TLS for the discovery service using rladmin:
- Default: Allows both TLS and non-TLS connections
- Syntax:
rladmin cluster config sentinel_tls_mode <ssl_policy> ssl_policyvalues available:allowed- Allows both TLS and non-TLS connectionsrequired- Allows only TLS connectionsdisabled- Allows only non-TLS connections
To set the minimum TLS protocol for the discovery service using rladmin:
- Default minimum TLS protocol: TLSv1.2
- Syntax:
rladmin cluster config min_sentinel_TLS_version <TLS_Version> - TLS versions available:
- For TLSv1.2 - 1.2
- For TLSv1.3 - 1.3
To enforce a minimum TLS version for the discovery service, run the following commands:
-
Allow only TLS connections:
rladmin cluster config sentinel_tls_mode required -
Set the minimal TLS version:
rladmin cluster config min_sentinel_TLS_version 1.2 -
Restart the discovery service on all cluster nodes to apply your changes:
supervisorctl restart sentinel_service