Connect to Amazon Web Services Transit Gateway
| Redis Cloud |
|---|
Amazon Web Services (AWS) Transit Gateway acts as a Regional virtual router for traffic flowing between your virtual private cloud(s) (VPCs) and on-premises networks. You can attach different resources to your Transit Gateway which include:
- One or more VPCs
- One or more virtual private network (VPN) connections
- One or more AWS Direct Connect gateways
- One or more Transit Gateway Connect attachments
- One or more transit gateway peering connections
You can connect your Redis Cloud Pro subscription to a Transit Gateway which is attached to the VPC of your application. This lets your application connect securely to your Redis Cloud database while optimizing performance.
Considerations
You can use Transit Gateway as an alternative to VPC peering, or you can enable both for your subscription.
Compared to VPC peering, Transit Gateway:
-
Supports complex network topologies, such as multiple VPCs or site-to-site VPNs.
-
Uses security groups and network ACLs to control traffic between VPCs.
-
Has a higher network latency and cost than VPC peering due to Transit Gateway infrastructure costs.
Consider using VPC peering and Transit Gateway in parallel for the following situations:
-
When migrating from one connectivity solution to the other.
-
If different applications need to connect to the same database but have different latency or security requirements.
Prerequisites
Before you can set up Transit Gateway, you need to:
-
Create a database with Redis Cloud Pro from the Redis Cloud console.
-
Create a transit gateway from the AWS VPC console in the same region as your database.
AWS Transit Gateway
To set up Transit Gateway:
-
Add consumer CIDRs to the attachment.
-
Update AWS route tables with the Redis Cloud producer CIDRs.
Associate resource share with Redis Cloud
In this step, you will associate your resource share with your subscription's AWS account. You can do this either in the AWS console or with the AWS CLI.
AWS Console
To use the AWS console to set up the resource share:
-
From the Redis Cloud console, select the Subscriptions menu and then select your subscription from the list.
-
Select Connectivity > Transit Gateway to view the transit gateway settings.
-
In the Share Transit Gateway section, select Copy under AWS console to copy the Redis AWS Account number.
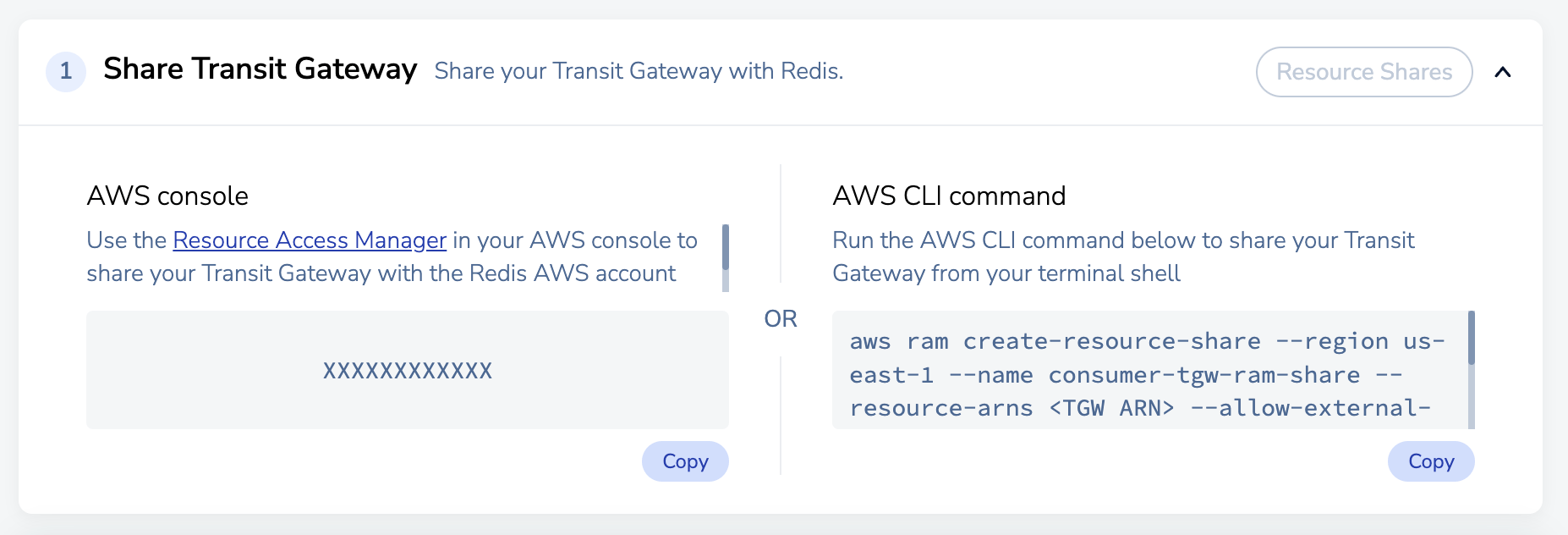
-
If you don't have a resource share for your transit gateway, follow the guide to create a resource share in the AWS resource access manager. If you do, follow the guide to update the resource share to include the provided AWS account as an Allowed Principal.
During the Grant access to principals step, select AWS Account in the Select principal type field. Enter the copied AWS account number in the Enter an AWS Account ID field.
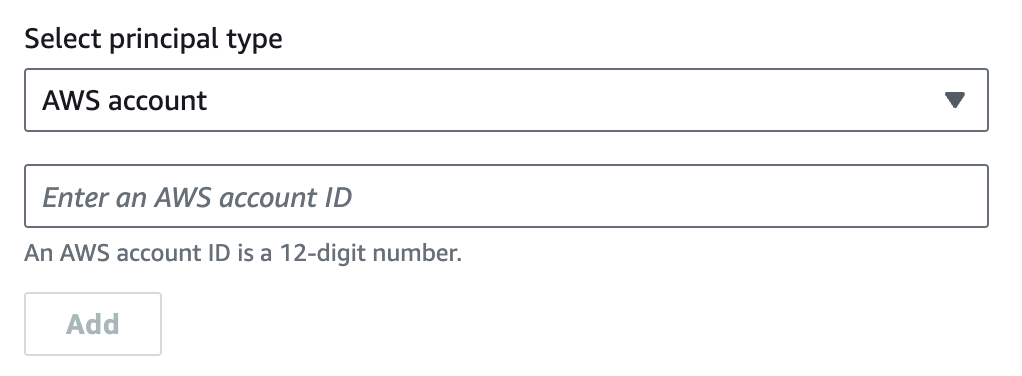
After the principal is added, it may take some time before it is associated. You can see the status of the principals under Shared Principals in the resource share page.
AWS CLI
To use the AWS CLI to set up the resource share:
-
From the Redis Cloud console, select the Subscriptions menu and then select your subscription from the list.
-
Select Connectivity > Transit Gateway to view the transit gateway settings.
-
In the Share Transit Gateway section, select Copy under AWS CLI Command to copy the Redis AWS Account number.

-
Enter the copied CLI command into a terminal shell. Replace
<TGW ARN>with the Amazon resource name of your transit gateway.
Accept resource share and create attachment
After you've associated the Redis AWS account with your resource share, you must accept the resource share in the Redis Cloud console.
-
In your Redis Cloud subscription's Transit Gateway settings, you should now see that a Resource Share is available. Select Resource Shares to view the resource share you initiated.

-
Select Accept to associate the Resource Share with your Redis Cloud console account.
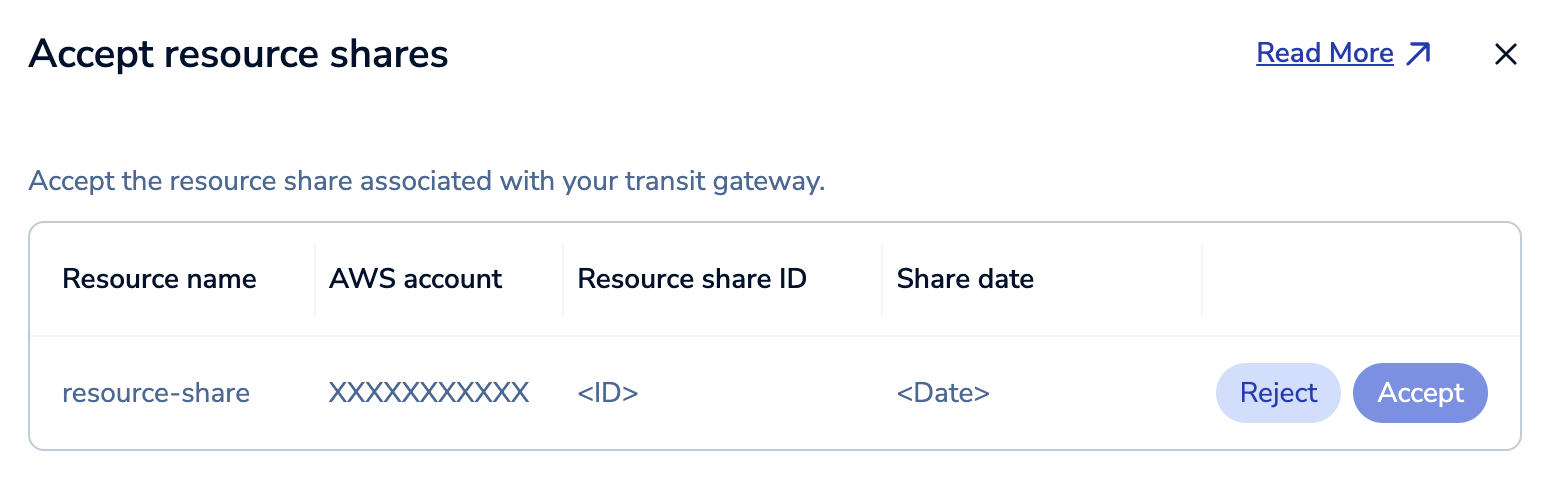
-
Select Close to close the Accept resource shares section.
-
You will now see your transit gateway in the Transit Gateways section. After the TGW status is Available, select Create Attachment under Attachment status.

This will request a peering attachment representing Redis's AWS account to the Transit Gateway.
-
If your transit gateway does not automatically accept peering attachment requests, the attachment will be in Pending acceptance status. Follow the guide to Accept a peering attachment request from the AWS VPC console.
Add consumer CIDRs
-
In your Redis Cloud subscription's Transit Gateway settings, in the Transit Gateways section, select Add CIDRs under Consumer CIDRs.
-
Enter the IPv4 CIDR of the VPC you want to connect to that is also connected to your transit gateway. To find this, go to the AWS VPC console and select Your VPCs.
Select Add to add another CIDR if needed.

Select Save to save your changes.
Update AWS route tables
To finish Transit gateway setup, update your route tables for the peering connection with the following details:
-
In the Destination field, enter the producer deployment CIDRs.
You can find the producer deployment CIDRs on the Redis Cloud console in the Transit Gateway settings by selecting More actions > View Attachment in the Transit Gateway section.

-
In the Target field, select Transit Gateway and select the relevant Transit gateway ID.
After Transit gateway is established, we recommend switching your application connection string to the private endpoint.
Continue learning with Redis University
See the Redis Cloud security overview course to learn more.