Tutorial
How to Handle Digital Identity Validation Using Redis (in Fraud Detection)
February 26, 202620 minute read
TL;DR:Use Redis Streams for inter-service communication and Redis JSON for storage to build a real-time digital identity validation system. At login, capture device fingerprints (browser agent, IP address) and store them in Redis. At checkout, compare the current session's fingerprint against stored login identities to calculate a risk score between 0 (no match) and 1 (full match), flagging suspicious activity before processing transactions.
#What you'll learn
- What digital identity is and why it matters for fraud prevention
- Why Redis is well-suited for real-time identity validation
- How to store digital identities using Redis Streams and JSON
- How to calculate identity risk scores by comparing device fingerprints
- How to validate identities at checkout in a microservices architecture
As the digital landscape continues to evolve, the need for robust security measures to protect users and organizations becomes ever more critical. Digital identity validation and fraud detection are essential components of any comprehensive security plan. This article will explore the significance of digital identity validation, the challenges faced in this area, and a solution to digital identity validation using Redis.
#What is Know Your Customer (KYC) and why does it matter?
"Know Your Customer" (KYC) regulations refer to a set of policies and procedures that financial institutions and other regulated businesses must follow to verify the identity of their customers. Customer details can be like name, address, date of birth, and other government-issued identification documents.
As part of KYC, businesses must assess the potential risk posed by each customer and conduct ongoing monitoring of their transactions and behavior to detect any suspicious activity. KYC regulations are enforced by regulatory authorities, and failure to comply can result in financial penalties and reputation damage.
KYC regulations are intended to prevent money laundering, terrorist financing, and other illicit activities. Financial services companies are combating the use of stolen identity information by reducing reliance on static methods for verifying identity (Knowledge-Based Authentication, or KBA) and instead moving to digital identities.
#What is a digital identity?
Digital identity refers to the collection of attributes and identifiers that represent an individual online. These may include names, email addresses, phone numbers, usernames, and biometrics, among others. Digital identity validation is the process of verifying that these attributes are accurate and belong to the entity they claim to represent.
Identity validation is crucial because it helps establish trust in digital environments, where face-to-face interaction is often not possible. It ensures that the parties involved in a transaction are who they claim to be, minimizing the risk of fraud, identity theft, and other cyber crimes.
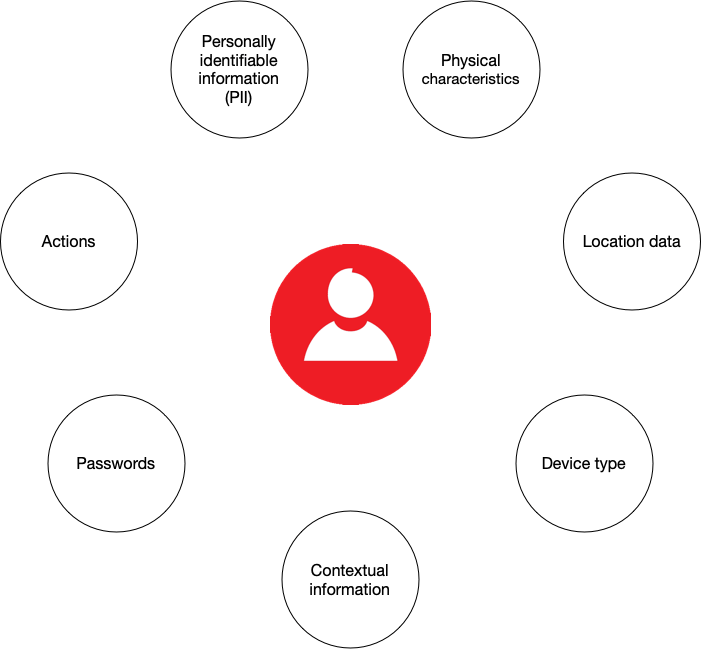
Digital identities consist of two parts:
- Static data: personally identifiable information (PII) such as name, address, and biometrics
- Dynamic data: behavioural and contextual information such as browsing history, device type, and location data. Dynamic digital identities are constantly updated based on the information available from each digital transaction.
Companies must monitor customer's every transaction and behaviour, then use stored digital identities to score the risk, identifying possible suspicious activity for a given transaction.
#Why should you use Redis for digital identity validation?
The following are the primary requirements of a storage layer for digital identities:
- Must maintain real-time read latency to fit within transaction SLA.
- Must have a flexible data model to store multiple unstructured data types such as behavioural, transactional, location, social/mobile and more.
These two factors are limiting for using traditional Relation Database Management Systems (RDBMS) to manage and validate digital identities in real time. While it is possible to use RDBMS to store digital identities, it is not the best choice for real-time validation of a flexible data model.
Redis Cloud, on the other hand, is optimized for high throughput, low latency, data flexibility, and real-time query performance, easily satisfying the first criterion. With sub-millisecond latency and hundreds of millions of operations per second across both read and write operations, it is well-suited for managing dynamic digital identity data. As the volume of data grows, we can expect near-linear scalability and 99.999% of uptime with Active-Active geo-replication.
Redis Cloud's flexible data model has native support for multiple data types, including JSON, hashes, streams, graphs and more. Additionally, it can process complex searches on structured and unstructured data, as well as filtering by numeric properties and geographical distances, making it easier to manage and query large datasets of digital identities.
#How is a digital identity validation microservice architected?
The e-commerce microservices application discussed in the rest of this tutorial uses the following architecture:
products service: handles querying products from the database and returning them to the frontendorders service: handles validating and creating ordersorder history service: handles querying a customer's order historypayments service: handles processing orders for paymentdigital identity service: handles storing digital identity and calculating identity scoreapi gateway: unifies services under a single endpointmongodb/ postgresql: serves as the primary database, storing orders, order history, products, etc.redis: serves as the stream processor and caching database
INFOYou don't need to use MongoDB/ Postgresql as your primary database in the demo application; you can use other prisma supported databases as well. This is just an example.
#How are digital identities stored in Redis?
Given we're discussing a microservices application, it makes sense to use a microservice for managing digital identities. Consider the following workflow outlining how digital identities are stored and retrieved from Redis:
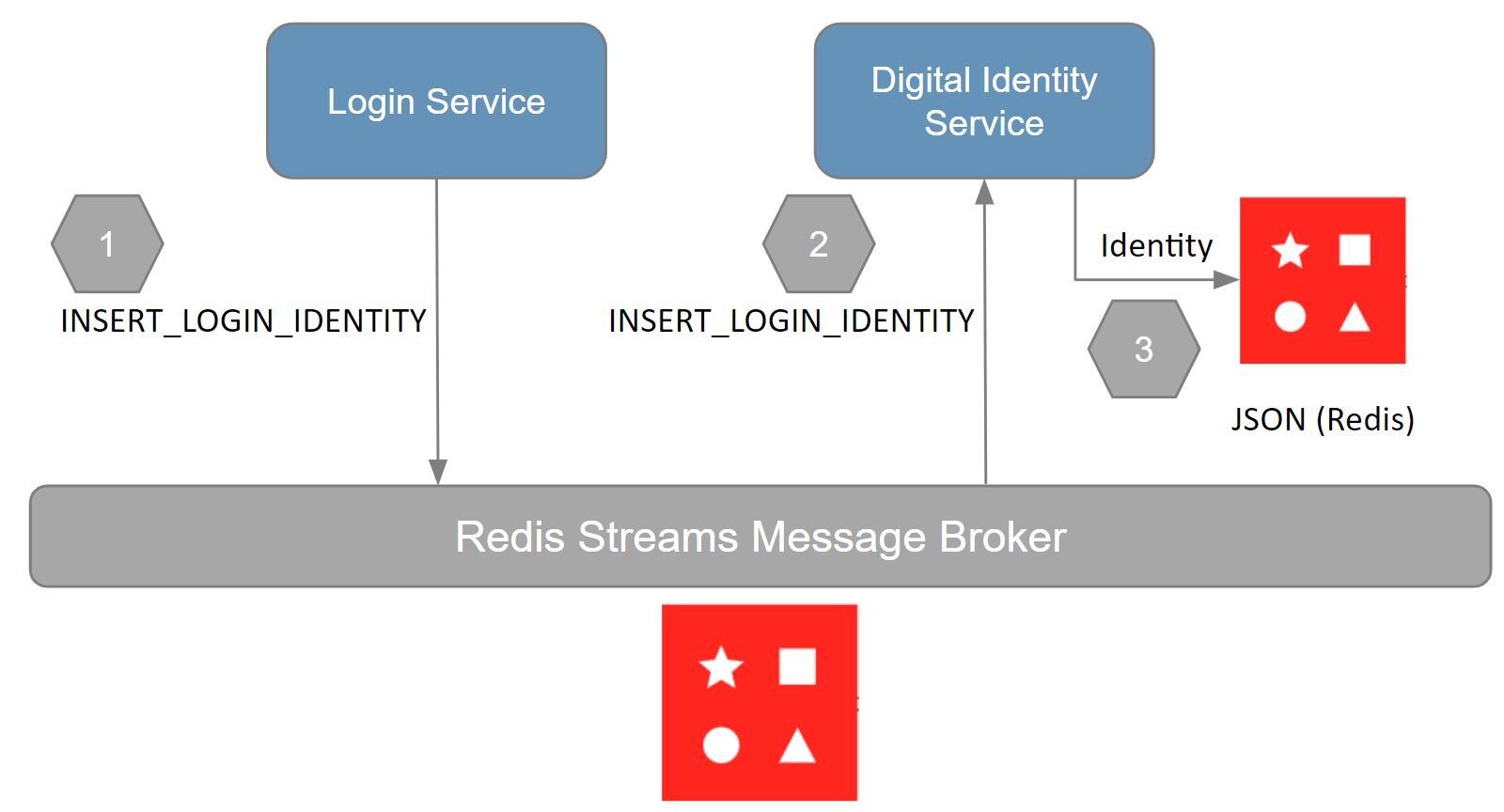
NOTEThe demo application doesn't have alogin service. All user sessions are currently authenticated in theapi gatewayservice. Sologin serviceis synonymous with theapi gatewaywith respect to the demo app.
The demo application uses redis streams for interservice communication. The following outlines the workflow, and the responsibilities of each service:
login service: stores the (user) digital identity as aINSERT_LOGIN_IDENTITYstream entry to redis
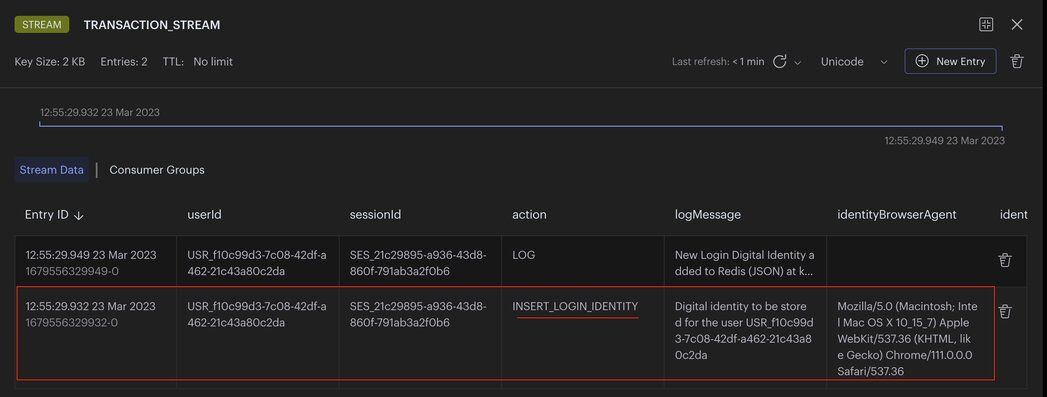
digital identity service: reads the identity from theINSERT_LOGIN_IDENTITYstreamdigital identity service: stores the identity as JSON to redis
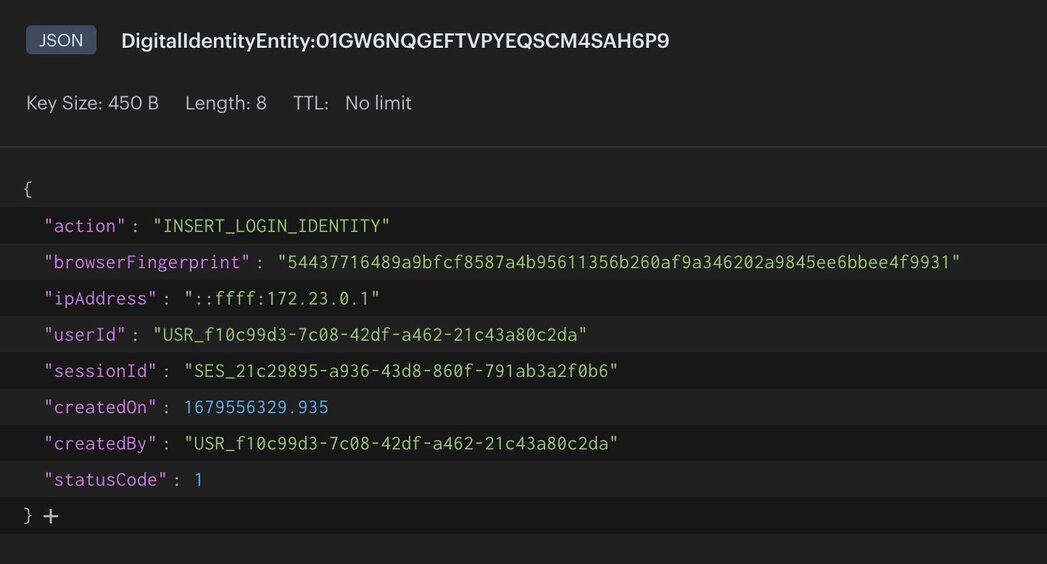
NOTEFor demo purposes, we are only using a few characteristics of a user's digital identity like IP address, browser fingerprint, and session. In a real-world application you should store more characteristics like location, device type, and prior actions taken for better risk assessment and identity completeness.
#How are digital identities validated at checkout?
In an e-commerce application, validating digital identities happens at checkout time. You want to make sure the customer is who they say they are before you attempt to process their order. To validate digital identities, we need to calculate the digital identity score, starting in the
orders service. The following outlines the workflow, and the responsibilities of each service: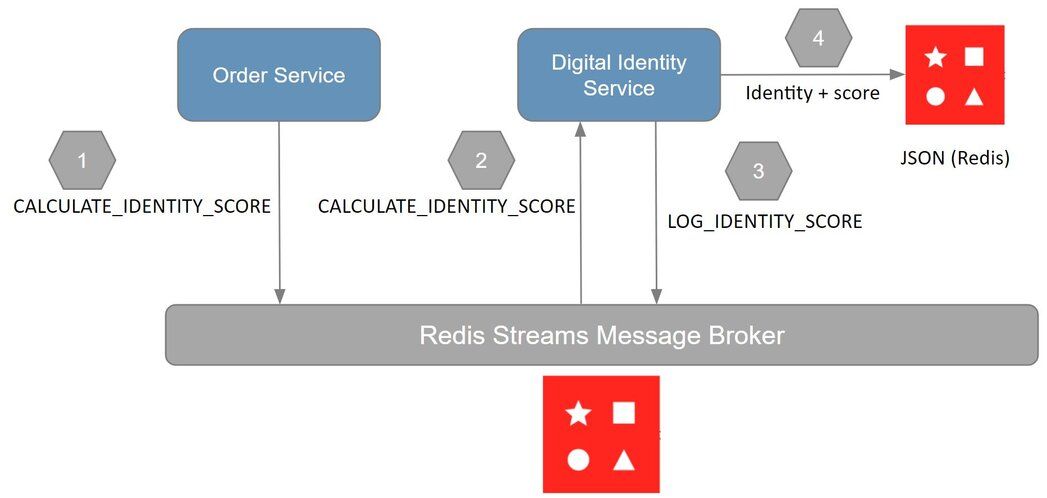
orders service: stores the digital identity in aCALCULATE_IDENTITY_SCOREredis stream event to calculate it's identity score
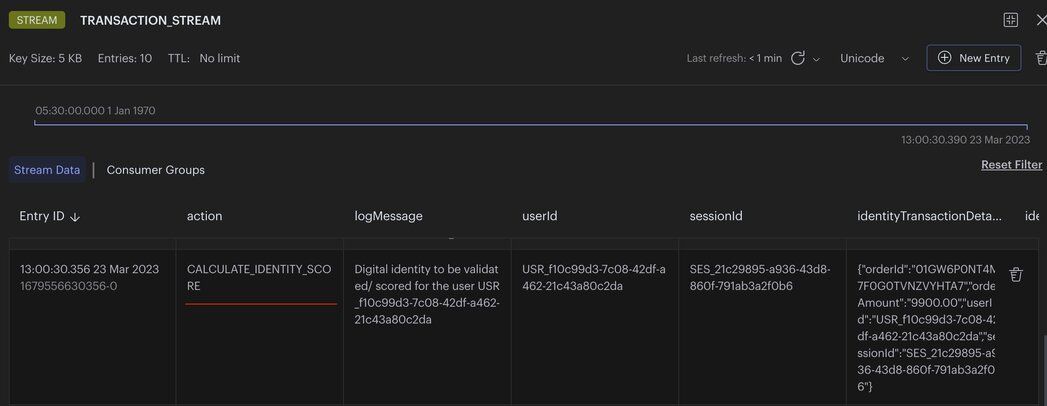
digital identity service: reads the identity from theCALCULATE_IDENTITY_SCOREstream eventdigital identity service: stores the identity with its calculated score as JSON
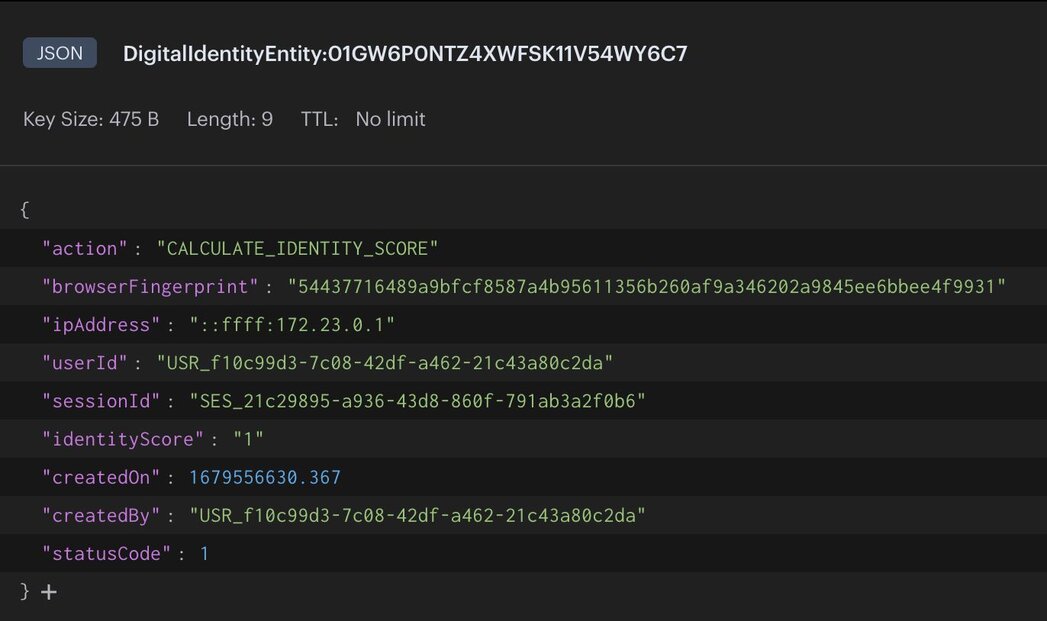
CAVEATEven though you may receive a score of “1” this only means the score has matched 100% against the measured properties only. We are only measuring digital aspects of the identity, which can be compromised. In a real-world scenario you would want to measure more characteristics like location, device type, session, etc. This is in addition to other contextual information for a complete transaction risk score.
#What does the e-commerce application frontend look like?
The e-commerce microservices application consists of a frontend, built using Next.js with TailwindCSS. The application backend uses Node.js. The data is stored in Redis and MongoDB/ Postgressql using Prisma. Below you will find screenshots of the frontend of the e-commerce app:
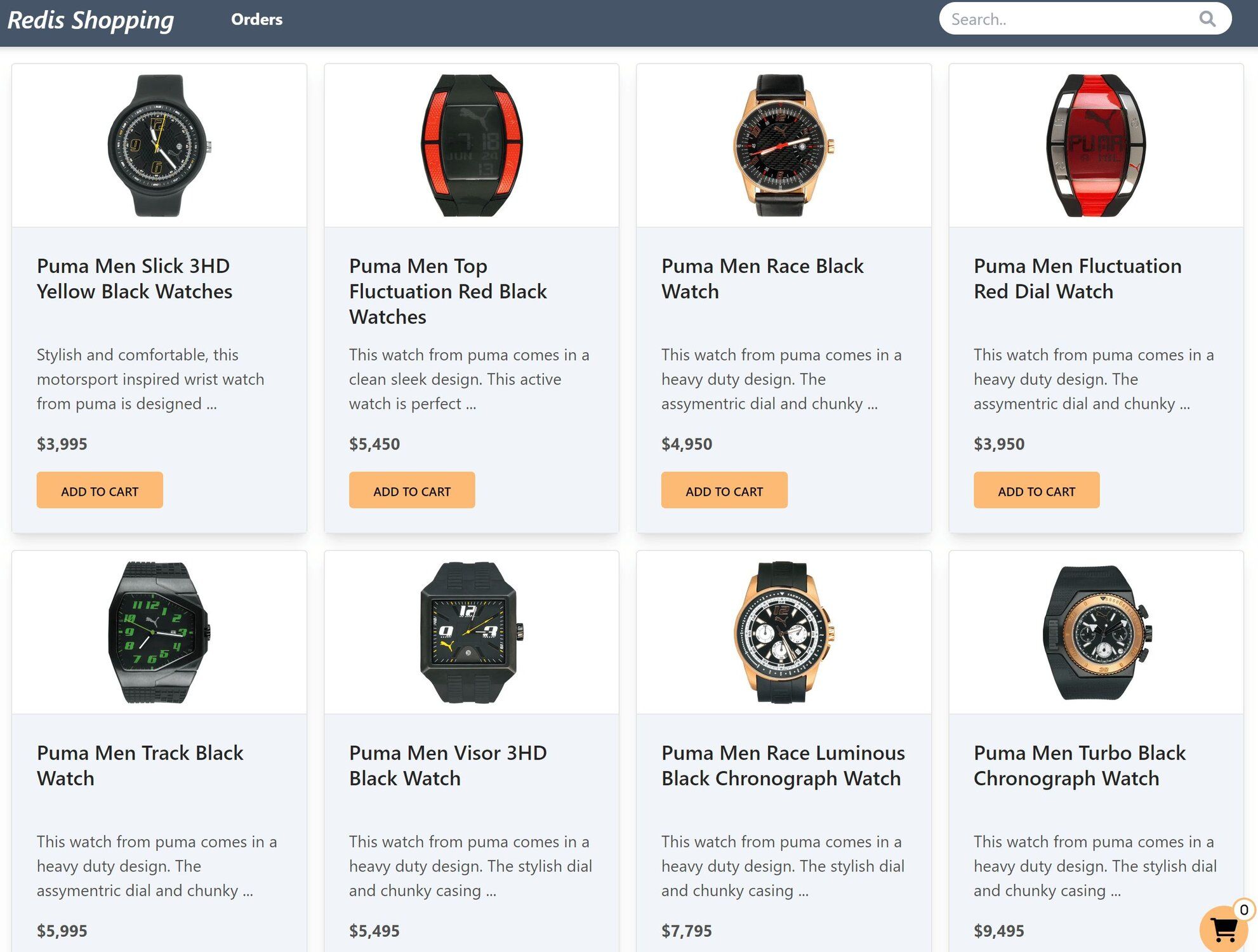
Dashboard: Shows the list of products with search functionality
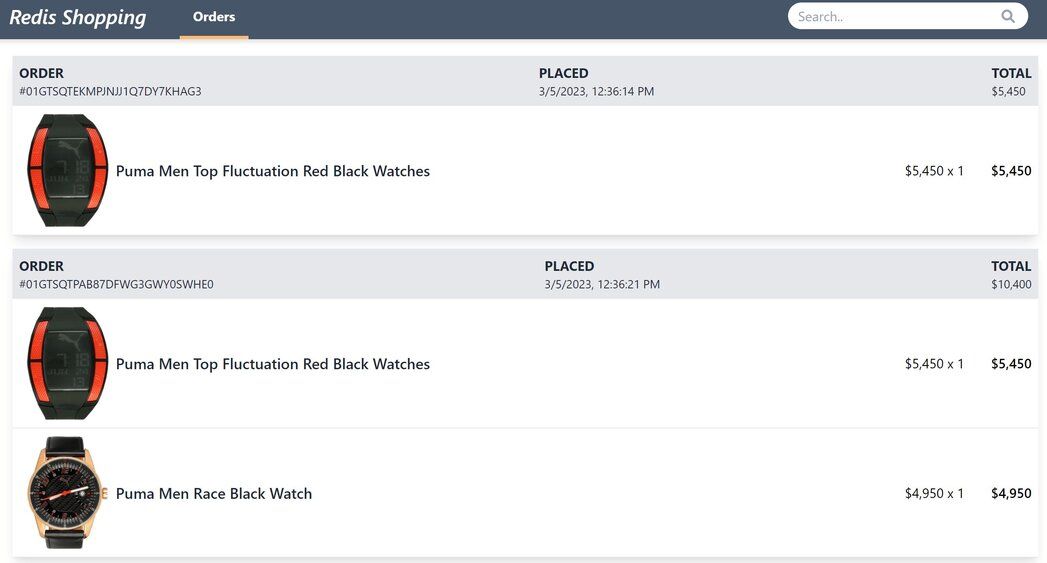
Order history: Once an order is placed, the Orders link in the top navigation bar shows the order status and history
GITHUB CODEBelow is a command to the clone the source code for the application used in this tutorialgit clone --branch v3.0.0 https://github.com/redis-developer/redis-microservices-ecommerce-solutions
#How do you build a digital identity validation microservice with Redis?
Now, let's go step-by-step through the process of storing, scoring, and validating digital identities using redis with some example code. For demo purposes, we are only using a few characteristics of a user's digital identity like IP address, browser fingerprint, and session. In a real-world application you should store more characteristics like location, device type, and prior actions taken for better risk assessment and identity completeness.
#How do you store digital identities in Redis?
login service: stores the (user) digital identity as aINSERT_LOGIN_IDENTITYstream entry to redis
digital identity service: reads the identity from theINSERT_LOGIN_IDENTITYstream
digital identity service: stores the identity as JSON to redis
#How do you validate digital identities and calculate risk scores?
orders service: stores the digital identity to be validated in aCALCULATE_IDENTITY_SCOREredis stream
digital identity service: reads the identity from theCALCULATE_IDENTITY_SCOREstream
digital identity service: stores the identity with score as JSON in redis
#Conclusion
Now you have learned how to use Redis to set up ongoing digital identity monitoring and scoring in a microservices application. This is also called "dynamic digital identity monitoring." Dynamic digital identities are constantly updated based on the information available from each digital transaction. By analyzing these transactions, businesses can build a comprehensive and up-to-date digital identity that includes both static and dynamic elements. These identities can then be scored to determine the risk that they pose to the business.
In addition to increasing security, digital identities can also improve the customer experience. By using the digital footprint left by a user, businesses can offer more personalized services and reduce friction in the authentication process.
Digital identity systems are typically designed to be interoperable and scalable, allowing for seamless integration with various applications and platforms.
#Next steps
Now that you've built a digital identity validation system, consider expanding your fraud detection capabilities:
- Add transaction risk scoring: Combine identity validation with transaction risk scoring to assess both the user and the transaction for a more complete fraud prevention pipeline.
- Build a full fraud detection system: Learn how to tie these components together in the fraud detection system overview tutorial, which covers the complete architecture.
- Explore microservices patterns: Dive deeper into inter-service communication with Redis to understand how Redis Streams power event-driven architectures.
- Add more identity signals: Extend the identity service with location data, device type, and session history for more accurate risk scoring.
#Additional resources
Redis Streams
- Explore streams in detail in the Redis University course on Redis Streams
- Check out our e-book on Understanding Streams in Redis and Kafka: A Visual Guide
General
- Redis YouTube channel
- Clients like Node Redis and Redis om Node help you to use Redis in Node.js applications.
- Redis Insight : To view your Redis data or to play with raw Redis commands in the workbench
- Try Redis Cloud for free

