Configure database defaults
Cluster-wide policies that determine default settings when creating new databases.
| Redis Software |
|---|
Database defaults are cluster-wide policies that determine default settings when creating new databases.
Edit database defaults
To edit default database configuration using the Cluster Manager UI:
-
On the Databases screen, select
 to open a list of additional actions.
to open a list of additional actions. -
Select Database defaults.
-
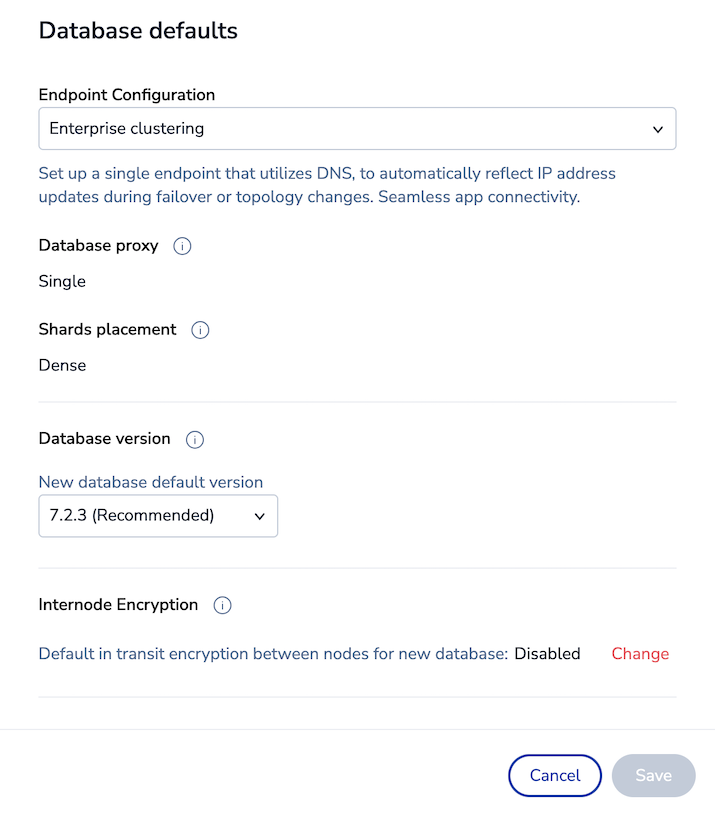
Configure database defaults.
-
Select Save.
Database defaults
Endpoint configuration
You can choose a predefined endpoint configuration to use the recommended database proxy and shards placement policies for your use case. If you want to set these policies manually instead, select Custom endpoint configuration.
| Endpoint configuration | Database proxy | Shards placement | Description | |
|---|---|---|---|---|
| Enterprise clustering | Single | Dense | Sets up a single endpoint that uses DNS to automatically reflect IP address updates after failover or topology changes. | |
| Using a load balancer | All nodes | Sparse | Configure Redis with a load balancer like HAProxy or Nginx for environments without DNS. | |
| Multiple endpoints | All primary shards | Sparse | To set up multiple endpoints, enable OSS Cluster API in the database settings and ensure client support. Clients initially connect to the primary node to retrieve the cluster topology, which allows direct connections to individual Redis proxies on each node. | |
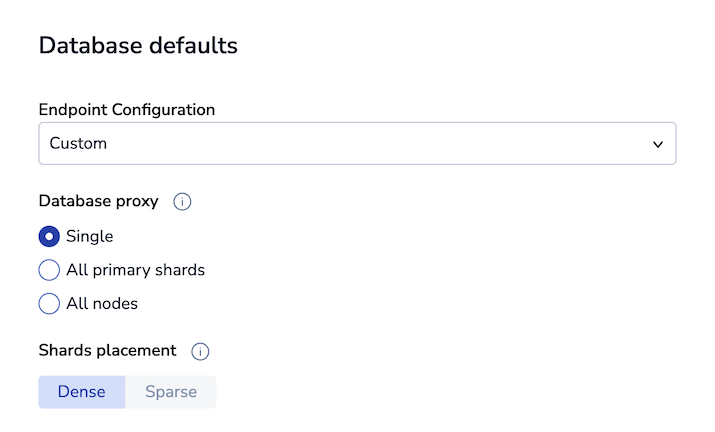
| Custom | Single, all primary shards, or all nodes | Dense or sparse | Manually choose default database proxy and shards placement policies. |
Database proxy
Redis Software uses proxies to manage and optimize access to database shards. Each node in the cluster runs a single proxy process, which can be active (receives incoming traffic) or passive (waits for failovers).
You can configure default proxy policies to determine which nodes' proxies are active and bound to new databases by default.
To configure the default database proxy policy using the Cluster Manager UI:
-
Select a predefined Endpoint Configuration to use a recommended database proxy policy, or choose Custom to set the policy manually. Changing the database proxy default in the Cluster Manager UI affects both sharded and non-sharded proxy policies.
Non-sharded proxy policy
To configure the default proxy policy for non-sharded databases, use one of the following methods:
-
rladmin tune cluster default_non_sharded_proxy_policy { single | all-master-shards | all-nodes } -
Update cluster policy REST API request:
PUT /v1/cluster/policy { "default_non_sharded_proxy_policy": "single | all-master-shards | all-nodes" }
Sharded proxy policy
To configure the default proxy policy for sharded databases, use one of the following methods:
-
rladmin tune cluster default_sharded_proxy_policy { single | all-master-shards | all-nodes } -
Update cluster policy REST API request:
PUT /v1/cluster/policy { "default_sharded_proxy_policy": "single | all-master-shards | all-nodes" }
Shards placement
The default shard placement policy determines the distribution of database shards across nodes in the cluster.
Shard placement policies include:
-
dense: places shards on the smallest number of nodes. -
sparse: spreads shards across many nodes.
To configure default shard placement, use one of the following methods:
-
Cluster Manager UI:
-
Select a predefined Endpoint Configuration to use a recommended shards placement policy, or choose Custom to set the policy manually.

-
rladmin tune cluster default_shards_placement { dense | sparse } -
Update cluster policy REST API request:
PUT /v1/cluster/policy { "default_shards_placement": "dense | sparse" }
Database version
New databases use the default Redis database version unless you select a different Database version when you create a database in the Cluster Manager UI or specify the redis_version in a create database REST API request.
To configure the Redis database version, use one of the following methods:
-
Cluster Manager UI: Edit Database version in Database defaults
-
rladmin tune cluster default_redis_version <x.y> -
Update cluster policy REST API request:
PUT /v1/cluster/policy { "default_provisioned_redis_version": "x.y" }
Internode encryption
Enable internode encryption to encrypt data in transit between nodes for new databases by default.
To enable or turn off internode encryption by default, use one of the following methods:
-
Cluster Manager UI: Edit Internode Encryption in Database defaults
-
rladmin tune cluster data_internode_encryption { enabled | disabled } -
Update cluster policy REST API request:
PUT /v1/cluster/policy { "data_internode_encryption": <boolean> }