SAML single sign-on
Redis Cloud supports both IdP-initiated and SP-initiated single sign-on (SSO) with SAML (Security Assertion Markup Language). You can use any identity provider to integrate with Redis Cloud as long as it supports the SAML protocol, or you can refer to integration guides for a few specific providers.
| Redis Cloud |
|---|
Redis Cloud supports both IdP-initiated and SP-initiated single sign-on (SSO) with SAML (Security Assertion Markup Language).
You cannot use SCIM (System for Cross-domain Identity Management) to provision Redis Cloud users. However, Redis Cloud supports just-in-time (JIT) user provisioning, which means Redis Cloud automatically creates a user account the first time a new user signs in with SAML SSO.
SAML SSO overview
When SAML SSO is enabled, the identity provider (IdP) admin handles SAML user management instead of the Redis Cloud account owner.
You can use any identity provider to integrate with Redis Cloud as long as it supports the SAML protocol. You can also refer to these integration guides for several popular identity providers:
- Auth0 SAML integration
- AWS IAM Identity Center SAML integration
- Azure Active Directory SAML integration
- Google Workspace integration
- Okta SAML integration (Generic)
- Okta SAML integration (Org2Org)
- PingIdentity SAML integration
After you activate SAML SSO for a Redis Cloud account, all existing local users for the account, except for the user that set up SAML SSO, are converted to SAML users and are required to use SAML SSO to sign in. Before they can sign in to Redis Cloud, the identity provider admin needs to set up these users on the IdP side and configure the redisAccountMapping attribute to map them to the appropriate Redis Cloud accounts and roles.
IdP-initiated SSO
With IdP-initiated single sign-on, you can select the Redis Cloud application after you sign in to your identity provider (IdP). This redirects you to the Redis Cloud console and signs you in to your SAML user account.
SP-initiated SSO
You can also initiate single sign-on from the Redis Cloud console. This process is known as service provider (SP)-initiated single sign-on.
-
From the Redis Cloud console's sign-in screen, select SSO.

-
Enter the email address associated with your SAML user account.
-
Select the Login button.
-
If you already have an active SSO session with your identity provider, this signs you in to your SAML user account.
-
Otherwise, the SSO flow redirects you to your identity provider's sign in screen. Enter your IdP user credentials to sign in. This redirects you back to the Redis Cloud console and automatically signs in to your SAML user account.
-
Multi-factor authentication
The account owner remains a local user and should set up multi-factor authentication (MFA) to help secure their account. After SAML activation, the account owner can set up additional local bypass users with MFA enabled.
If MFA enforcement is enabled, note that Redis Cloud does not enforce MFA for SAML users since the identity provider handles MFA management and enforcement.
Set up SAML SSO
To set up SAML single sign-on for a Redis Cloud account:
-
Set up a SAML app to integrate Redis Cloud with your identity provider.
-
Download service provider metadata and upload it to your identity provider.
Verify domain ownership in Redis Cloud
Before you set up SAML SSO in Redis Cloud, you must verify that you own the domain(s) associated with your SAML setup.
-
Sign in to Redis Cloud with the email address associated with the SAML user you set up with your identity provider.
-
Select Access Management from the Redis Cloud console menu.
-
Select Single Sign-On.
-
Select the Setup SAML SSO button:

-
From the SAML screen of the Redis Cloud console, you must verify you own the domains associated with your SAML configuration. Select Add domain to open the Manage domain bindings panel.

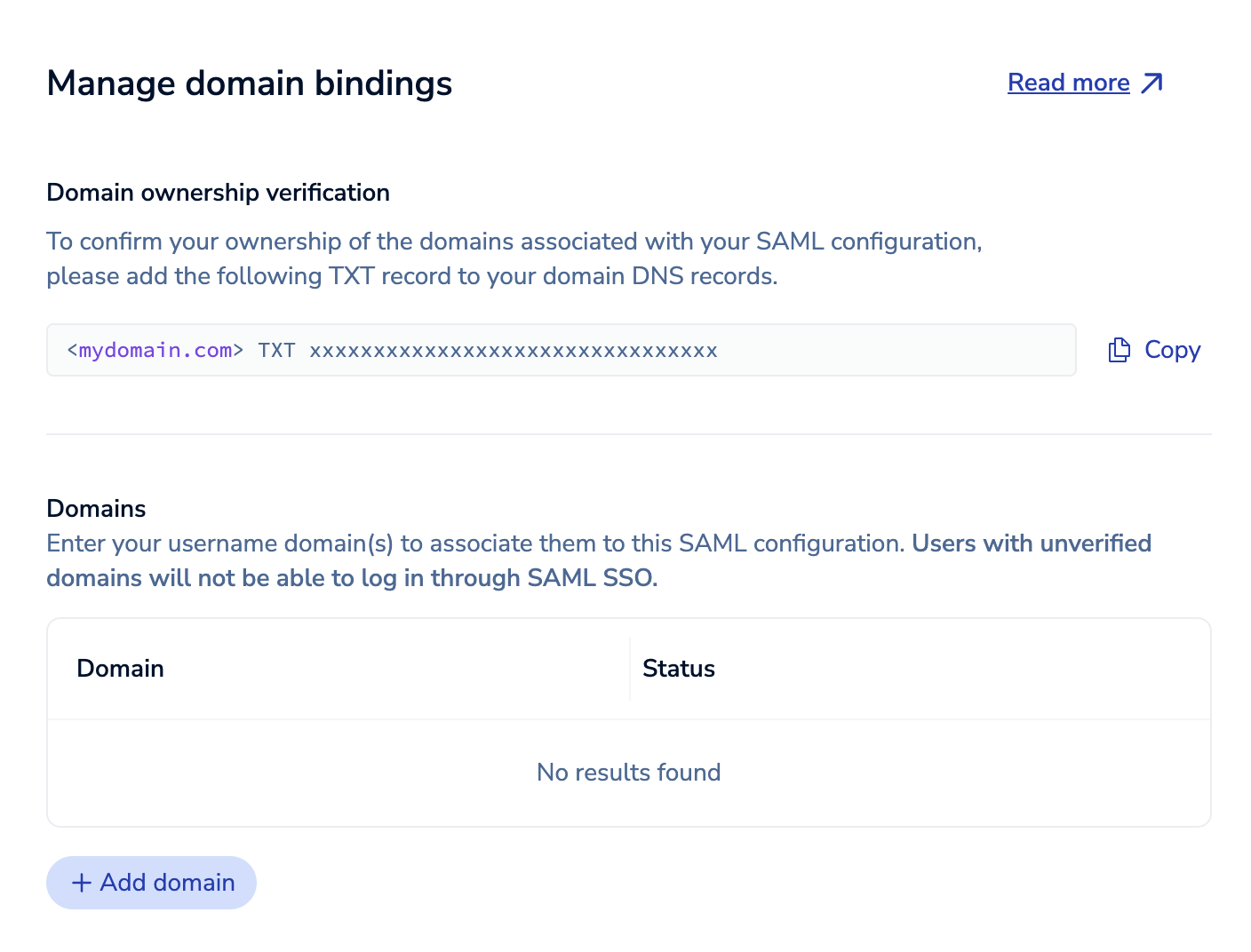
-
Select Copy to copy the provided TXT DNS record. For each domain you want to associate with your SAML setup, add the copied TXT record to its DNS records.
-
Select Add domain to add a domain.

-
Enter the domain name and select
 to save it, or select
to save it, or select
 to cancel.
to cancel.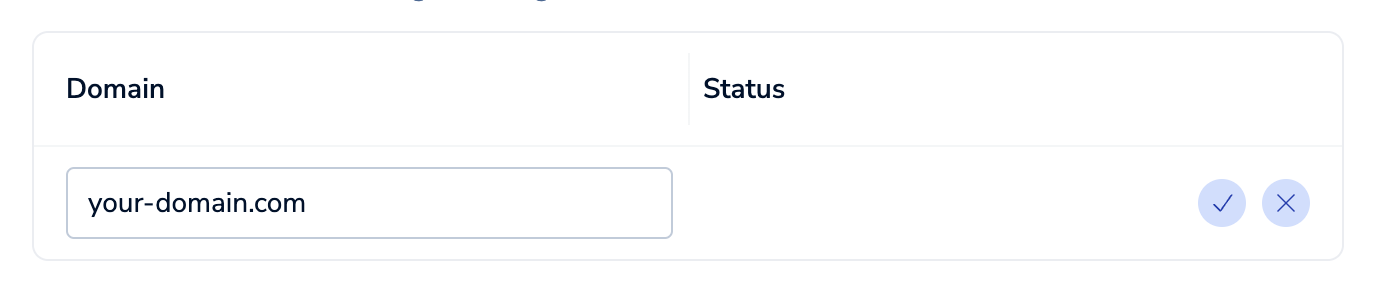
-
After you save the domain name, its status is Pending. Select Verify to verify it.
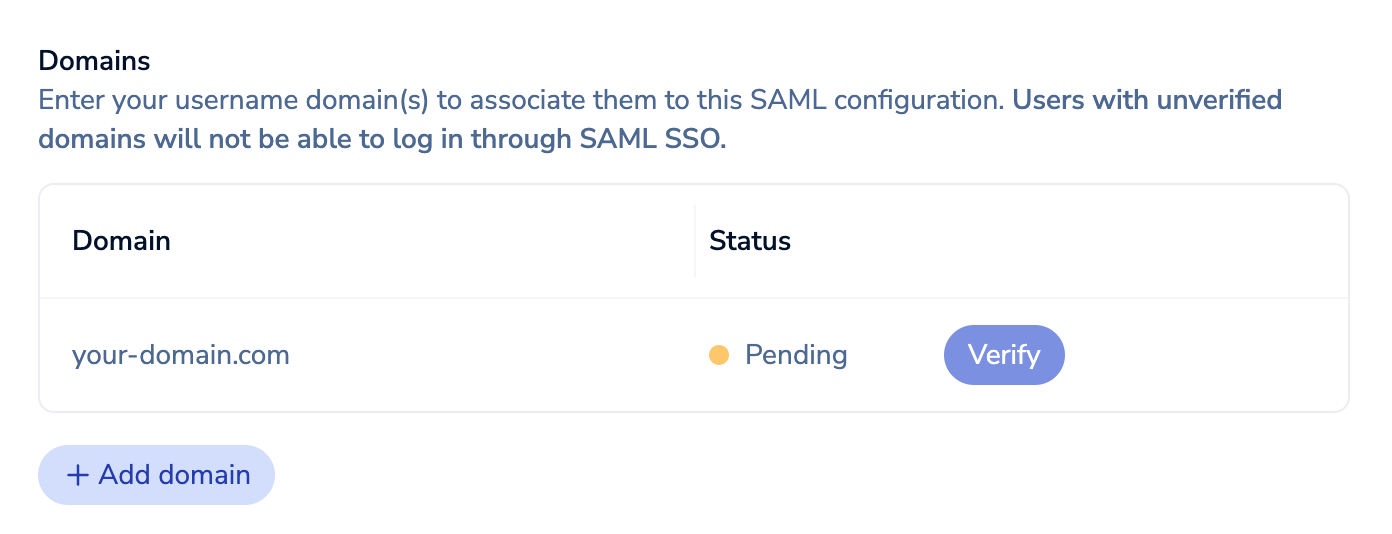
We'll check the domain's DNS records for the provided TXT record. If the TXT record does not exist or we can't resolve your domain, we won't be able to verify the domain and users with that domain won't be able to sign in using SAML SSO.
Select
 to delete a domain if it was added by mistake.
to delete a domain if it was added by mistake.If we find the TXT record, the domain's status will change to Verified.
You can select Add domain to add another domain.
-
Select Close to close the domain binding panel.

After you verify at least one domain, you can select Manage domains to open the Manage domain bindings panel again and add or verify more domains.
Set up SAML app
Set up a SAML app to integrate Redis Cloud with your identity provider:
-
Sign in to your identity provider's admin console.
-
Create or add a SAML integration app for the service provider Redis Cloud.
-
Set up your SAML service provider app so the SAML assertion contains the following attributes:
Attribute name
(case-sensitive)Description FirstName User's first name LastName User's last name Email User's email address (used as the username in the Redis Cloud console) redisAccountMapping Key-value pair of a lowercase role name (owner, member, manager, billing_admin, or viewer) and the user's Redis Cloud Account number found in the account settings For
redisAccountMapping, you can add the same user to multiple SAML-enabled accounts using one of these options:-
A single string that contains a comma-separated list of account/role pairs
<saml2:Attribute Name="redisAccountMapping" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified"> <saml2:AttributeValue xsi:type="xs:string" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> 12345=owner,54321=manager </saml2:AttributeValue> </saml2:Attribute> -
Multiple strings, where each represents a single account/role pair
<saml2:Attribute Name="redisAccountMapping" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified"> <saml2:AttributeValue xsi:type="xs:string" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> 12345=owner </saml2:AttributeValue> <saml2:AttributeValue xsi:type="xs:string" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> 54321=manager </saml2:AttributeValue> </saml2:Attribute>
Note:To confirm the identity provider's SAML assertions contain the required attributes, you can use a SAML-tracer web developer tool to inspect them. -
-
Set up any additional configuration required by your identity provider to ensure you can configure the
redisAccountMappingattribute for SAML users.If your identity provider lets you configure custom attributes with workflows or group rules, you can set up automation to configure the
redisAccountMappingfield automatically instead of manually.
Configure SAML in Redis Cloud
After you set up the SAML integration app and create a SAML user in your identity provider, you need to configure your Redis Cloud account to set up SAML SSO.
-
Sign in to Redis Cloud with the email address associated with the SAML user you set up with your identity provider.
-
Select Access Management from the Redis Cloud console menu.
-
Select Single Sign-On.
-
Verify at least one domain if you haven't.
-
Configure the Identity Provider metadata settings.
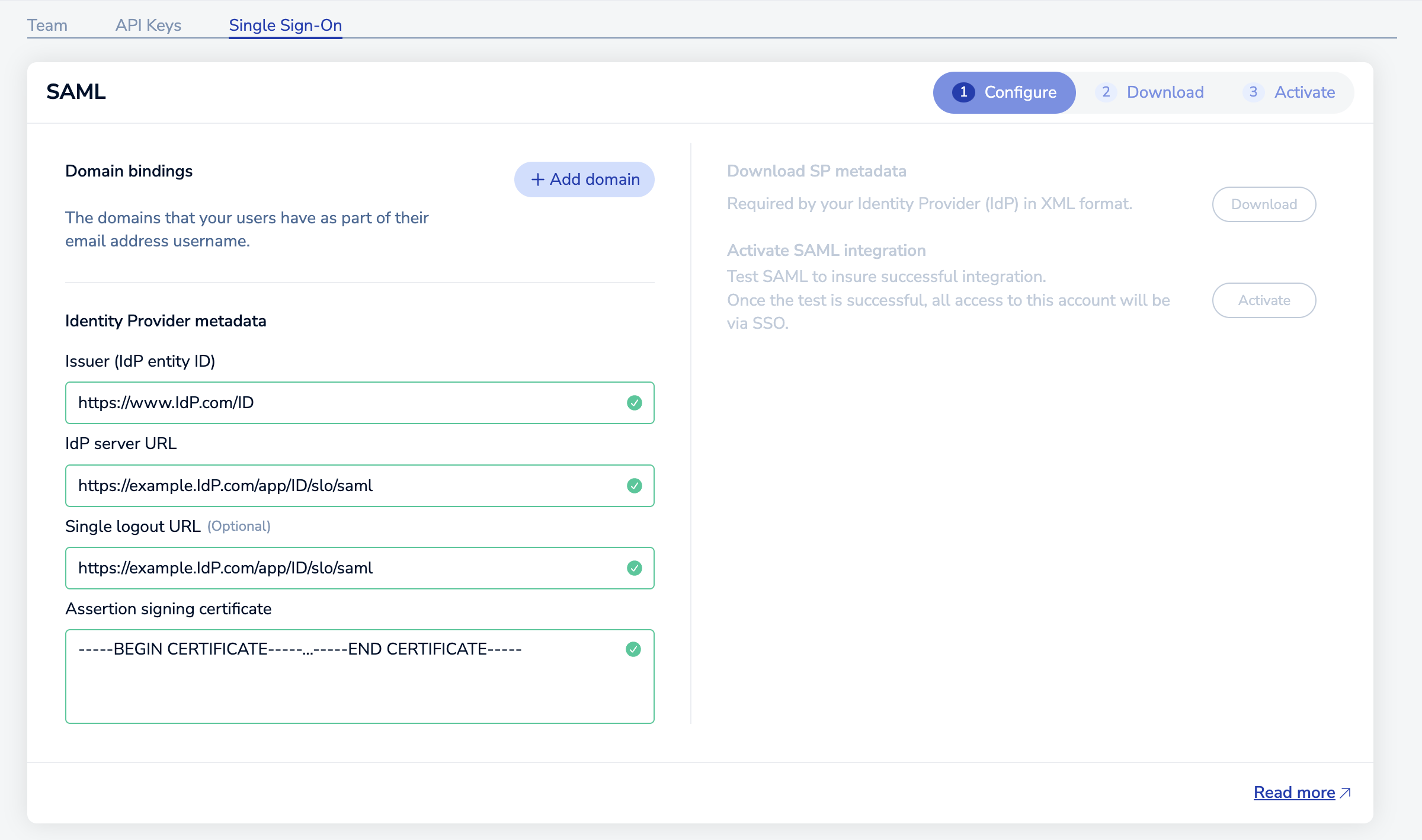
To do so, you need the following metadata values from your identity provider:
Setting Description Issuer (IdP entity ID) The unique entity ID for the identity provider IdP server URL The identity provider's HTTPS URL for SAML SSO Single logout URL The URL used to sign out of the identity provider and connected apps (optional) Assertion signing certificate Public SHA-256 certificate used to validate SAML assertions from the identity provider To find these metadata values, see your identity provider's documentation.
-
Select Enable.

-
From the SAML activation dialog box, select Continue.
Download service provider metadata
Next, you need to download the service provider metadata for Redis Cloud and use it to finish configuring the SAML integration app for your identity provider:
-
Select the Download button to download the service provider metadata in XML format.
-
Sign in to your identity provider's admin console.
-
Configure the Redis Cloud service provider app with the downloaded XML.
-
Some identity providers let you upload the XML file directly.
-
Others require you to manually configure the service provider app with specific metadata fields, such as:
XML attribute Value Description EntityDescriptor's entityID https:// auth.redis.com /saml2/service-provider /<ID>Unique URL that identifies the Redis Cloud service provider AssertionConsumerService's Location https:// auth.redis.com /sso/saml2/<ID>The service provider endpoint where the identity provider sends a SAML assertion that authenticates a user -
To use IdP-initiated SSO with certain identity providers, you also need to set the RelayState parameter to the following URL:
https://cloud.redis.io/#/login/?idpId=<ID>Replace
<ID>so it matches theAssertionConsumerService LocationURL's ID.
To learn more about how to configure service provider apps, see your identity provider's documentation.
-
Activate SAML SSO
After you finish the required SAML SSO configuration between your identity provider and Redis Cloud account, you can test and activate SAML SSO.
All users associated with the account, excluding the local user you used to set up SAML SSO, are converted to SAML users on successful activation. They can no longer sign in with their previous sign-in method and must use SAML SSO instead. However, you can add local bypass users after SAML SSO activation to allow access to the account in case of identity provider downtime or other issues with SAML SSO.
To activate SAML SSO:
-
Sign out of any active SSO sessions with your identity provider.
-
For Activate SAML integration, select the Activate button.
-
From the Logout notification dialog, select Continue. This redirects you to your configured identity provider's sign-in screen.
-
Sign in with your identity provider.
-
When redirected to the Redis Cloud sign-in screen, you can either:
-
Sign in with your local credentials as usual.
-
Select SSO and enter the email address associated with the SAML user configured in your identity provider. Your user converts to a SAML user in Redis Cloud. Don't use this method if you want your user account to remain a local bypass user.
Note:If you see a SAML activation failed notification when redirected to the Redis Cloud sign-in screen, sign in with your local user credentials and review the SAML configuration for issues. -
After you activate SAML SSO, add a few local bypass users from the Team tab. Local bypass users should set up MFA for additional security.
Update configuration
If you change certain metadata or configuration settings after you set up SAML SSO, such as the assertion signing certificate, remember to do the following:
-
Update the SAML SSO configuration with the new values.
-
Download the updated service provider metadata and use it to update the Redis Cloud service provider app.
Link other accounts
After you set up SAML SSO for one account, you can link other accounts you own to the existing SAML configuration. This lets you use the same SAML configuration for SSO across multiple accounts.
Owner role assigned to your user account for all accounts you want to link. The same user must link each account to the original configuration.To link other accounts to an existing SAML SSO configuration:
-
Sign in to the Redis Cloud console with the account that has an existing SAML configuration.
-
Go to Access Management > Single Sign-On.
-
Select Get token.
Select Copy to copy the linking token.
-
Sign in to the account that you want to link to the SAML configuration. Go to Access Management > Single Sign-On and then enter the copied token into the Join an existing SAML configuration text box. Select the arrow to confirm.
After you do this, the owner of the original account will receive a request to link the new account to the SAML configuration.
-
Sign in with the original account and select Access Management > Single Sign-On. You should see the new account in the Unlinked accounts list.
-
Select Link account.

-
In the Convert existing users dialog, select Confirm conversion to finish linking the accounts.
Deactivate SAML SSO
Before you can deactivate SAML SSO for an account, you must sign in to the account as a local (non-SAML) user with the owner role assigned.
Deactivating SAML SSO for an account also removes any existing SAML-type users associated with the account.
To deactivate SAML SSO for a specific account:
-
In the Redis Cloud console, select your name to display your available accounts.
-
If the relevant account is not already selected, select it from the Switch account list.
-
Go to Access Management > Single Sign-On.
-
Select Deactivate SAML. This only deactivates SAML SSO for the current account. Other linked accounts continue to use this SAML SSO configuration.
-
Select Deactivate to confirm deactivation.
Deprovision SAML users
When a user is removed from your identity provider, their access to Redis Cloud should also be removed.
When you have revoked a user’s access to Redis Cloud, they cannot access the Redis Cloud console, but their API keys remain active. You can delete an API key to remove access.
To deprovision SAML users upon deletion, the identity provider admin can set up a webhook to automatically make the appropriate Cloud API requests. For more information about managing users with API requests, see Users in the Redis Cloud API documentation.